State-backed phishing attacks targeting military officials and journalists on Signal
German security authorities are warning that a likely state-backed hacking group is engaged in attempts at phishing senior political figures, military officials, diplomats, and investigative journalists across Germany and Europe via Signal.
The authorities also noted that while these attacks are likely perpetrated by a state-controlled cyber actor, there’s nothing stopping non-state actors and financially motivated cybercriminals from using the same approach.
The two approaches
The attackers are approaching targets directly inside the messaging app and guiding them into handing over access to their accounts.
An alert issued by the Federal Office for the Protection of the Constitution (BfV) and Federal Office for Information Security (BSI) on Friday outlines two versions of the attack.
In the first, the attacker poses as official Signal support (“Signal Support” or “Signal Security ChatBot”) and messages the target:
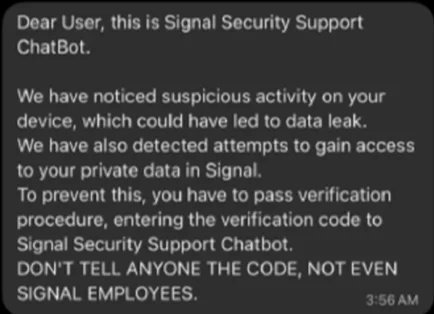
The phishing message (Source: German Federal Office for Information Security)
The message usually claims there is a security problem and that urgent action is needed. The target is told that providing a security PIN or a one-time verification code will prevent data loss and attackers accessing their account.
If the victim complies, the latter is what happens, because the attackers can then register the account on a device they control and effectively take it over.
In the second variant, the attacker tries to convince the target to scan a QR code, supposedly for a legitimate reason. In reality, the code links an additional device to the victim’s account. From that point on, the attacker can read messages and monitor conversations without immediately locking the user out.
Attackers thus gain ongoing access to private chats, group conversations, and contact lists. That can expose sensitive discussions, map out entire professional networks, and send messages while pretending to be the victim.
“Successful access to messenger accounts enables not only insight into confidential one-on-one communications but also the potential compromise of entire networks via group chats. In addition, sensitive contact structures can be reconstructed and used for further intelligence-gathering and/or criminal activities,” the authorities noted.
Report successful attacks to the authorities
The attackers are currently trying to trick targets using the Signal secure messaging app, though the authorities say that WhatsApp users can be similarly targeted because the two messaging service offer similar functionalities.
Users who fall victim to the first attack variant will know almost immediately. “The ‘Signal’ app indicates that your device is no longer registered, and incoming or outgoing messages are no longer possible,” the alert explains.
German authorities are advising Signal users to not respond to messages from supposed support accounts and to block and report them.
PINs should never be shared via messages, they added, and users should enable account protection features such as registration locks. Scanning QR codes should only happen when the user intentionally tries to link their own devices
Users should regularly review devices connected to their accounts (Settings > Linked Devices) and the authorities are urging users who know or suspect they have been targeted to contact them.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!
