DDoS attacks jump 358% compared to last year
Cloudflare says it mitigated 20.5 million DDoS attacks in the first quarter of 2025. This is a 358% increase compared to the same time last year. Their Q1 2025 DDoS report highlights a rise in the number and size of attacks, including some of the largest ever recorded.
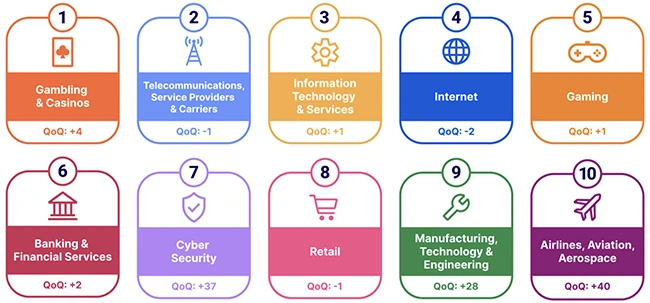
Map of top 10 most attacked industries in Q1 2025 (Source: Cloudflare)
Massive multi-vector attacks
One-third of the attacks, about 6.6 million, directly targeted Cloudflare’s own network infrastructure. These came during an intense 18-day multi-vector campaign that also hit hosting and service providers. Attack types included SYN floods, Mirai botnet attacks, and SSDP amplification attacks.
Researchers also reported more than 700 hyper-volumetric attacks, defined as exceeding 1 terabit per second (Tbps) or 1 billion packets per second (Bpps). On average, that’s about eight hyper-volumetric attacks every day. These were mostly UDP-based floods.
One of the most notable trends is the sheer speed and intensity of the largest attacks. In late April, Cloudflare mitigated attacks peaking at 6.5 Tbps and 4.8 billion packets per second. Both lasted less than a minute but could have overwhelmed unprotected systems. The attacks spilled into Q2 2025 and targeted a hosting provider.
Most DDoS attacks, however, remain relatively small. According to researchers, 99% of network-layer attacks stayed under 1 Gbps and 1 million packets per second. Still, even smaller attacks can saturate a link or knock down unprotected services.
Most victims unsure who’s behind attacks
The report emphasizes that attacks are increasingly short-lived. About 89% of network-layer attacks and 75% of HTTP attacks ended within 10 minutes. In cases of hyper-volumetric attacks, many lasted just 35 to 45 seconds. Cloudflare warns that manual mitigation is no longer feasible against attacks of this speed.
On the threat actor side, most victims said they didn’t know who was behind the attacks. Among those who did, competitors were blamed most often (39%), followed by suspected state-sponsored actors (17%), disgruntled users or customers (17%), self-inflicted DDoS incidents (11%), extortionists (11%), and former employees (6%).
The report also tracks emerging DDoS methods. CLDAP reflection attacks surged 3,488% quarter-over-quarter. ESP reflection attacks grew 2,301% during the same time. Both techniques take advantage of UDP traffic properties to reflect or amplify malicious traffic toward a victim.
Shift in DDoS targets
The top locations for DDoS attacks shifted this quarter. Germany rose to become the most attacked country, while Turkey jumped 11 spots to second place. China dropped two spots to third. In terms of industries, Gambling & Casinos became the most targeted, pushing Telecommunications to second.

Map of top 10 most attacked locations in Q1 2025 (Source: Cloudflare)
Researchers also identified changes in where attacks originate. Hong Kong became the leading source of DDoS traffic, followed by Indonesia and Argentina. Many attacks continue to originate from compromised infrastructure hosted by cloud providers. The top source ASNs included Hetzner, OVH, DigitalOcean, Contabo, and ChinaNet-Backbone.