Sinisa Markovic
Pompelmi: Open-source secure file upload scanning for Node.js
Software teams building services in JavaScript are adding more layers of defense to handle untrusted file uploads. An open-source project called Pompelmi aims to insert …

Microsoft sets new timeline for Sentinel transition to Defender portal
Microsoft has updated the timeline for transitioning the Microsoft Sentinel experience from the Azure portal to the Microsoft Defender portal from July 1, 2026 to March 31, …

Ex-Google engineer found guilty of stealing AI secrets
A federal jury in California convicted former Google software engineer Linwei Ding, also known as Leon Ding, on seven counts of economic espionage and seven counts of theft of …

EFF calls out major tech companies on encryption promises
The Electronic Frontier Foundation (EFF) has introduced a new campaign called Encrypt It Already, focused on expanding the use of end-to-end encryption in consumer technology …

Security work keeps expanding, even with AI in the mix
Board attention continues to rise, and security groups now operate closer to executive decision making than in prior years, a pattern reflected the Voice of Security 2026 …

Wearable tech adoption continues as privacy worries grow
Over 1 billion users wear devices for tracking steps, sleep, heart rate, and other personal metrics. These devices collect a continuous stream of sensitive data, often tied to …

France Travail fined €5 million for failing to protect job seeker data
France data protection authority CNIL has fined public employment agency France Travail €5 million for failing to ensure the security of personal data of job seekers. …

Conditional Access enforcement change coming to Microsoft Entra
Microsoft will change how Conditional Access policies are enforced in Microsoft Entra starting March 27, 2026, with a phased rollout continuing through June 2026. The change …

Google agrees to pay $135 million over Android data harvesting claims
Google agrees to pay $135 million to settle a proposed class action lawsuit brought by Android smartphone users over alleged unauthorized cellular data transmissions. After …

Samsung tackles shoulder surfing on Galaxy devices
Our phones hold our most personal details, and we use them everywhere. On the bus, in elevators, and while waiting in line, screens are often visible to people nearby. The …

French government abandons Zoom and Microsoft Teams over security concerns
France intends to phase out non-European videoconferencing platforms such as Zoom and Microsoft Teams from its public administration, opting instead for a nationally developed …
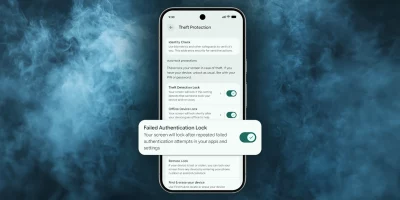
Android just got smarter at stopping snatch-and-run phone thefts
Google announced updates to the Android theft protection features that expand existing safeguards and make stolen devices harder to use. These updates are available on Android …