mobile security

European Commission hit by cyberattackers targeting mobile management platform
The European Commission’s mobile device management platform was hacked but the incident was swiftly contained and no compromise of mobile devices was detected, …

Samsung tackles shoulder surfing on Galaxy devices
Our phones hold our most personal details, and we use them everywhere. On the bus, in elevators, and while waiting in line, screens are often visible to people nearby. The …
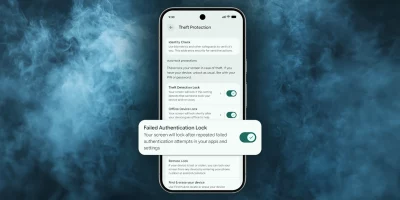
Android just got smarter at stopping snatch-and-run phone thefts
Google announced updates to the Android theft protection features that expand existing safeguards and make stolen devices harder to use. These updates are available on Android …

Uneven regulatory demands expose gaps in mobile security
Mobile networks carry a great deal of the world’s digital activity, which makes operators a frequent target for attacks. A study released by the GSMA shows that operators …

iOS security features you should use to protect your privacy
iOS 18 comes with several privacy and security features that many iPhone users overlook. Knowing how to use them can help you protect your personal information and control …

From cleaners to creepers: The risk of mobile privilege escalation
In this Help Net Security video, Nico Chiaraviglio, Chief Scientist at Zimperium, explores how Android apps can be abused to escalate privileges, giving attackers access to …

44% of mobile users encounter scams every day
Nearly half of of mobile users encounter mobile scams daily, with people in the US and UK more likely to be targeted than those in other regions, according to Malwarebytes. …

Phone theft is turning into a serious cybersecurity risk
Phone theft is a rising issue worldwide, and it’s more than just a property crime. It’s a serious cybersecurity threat. In the UK alone, the Metropolitan Police seizes 1,000 …

Mobile security is a frontline risk. Are you ready?
The mobile threat landscape has shifted. According to Zimperium’s 2025 Global Mobile Threat Report, attackers are now prioritizing mobile devices over desktops. For …

The UK’s phone theft crisis is a wake-up call for digital security
Phone theft is now commonplace in London. The Met Police recently revealed that it seizes 1,000 stolen phones weekly as it cracks down on organized criminal networks driving …

iOS devices face twice the phishing attacks of Android
2024 brought about countless new cybersecurity challenges including significant growth of the mobile threat landscape, according to Lookout. Threat actors, ranging from …

iOS devices more exposed to phishing than Android
The mobile threat landscape continues to grow at an alarming rate as cybercrime groups shift their tactics and target mobile devices in the early stages of their attacks, …
Featured news
Resources
Don't miss
- Criminals create business website to sell RAT disguised as RMM tool
- Ex-Google engineers charged with orchestrating high-tech secrets extraction
- Google cleans house, bans 80,000 developer accounts from the Play Store
- The CISO view of fraud risk across the retail payment ecosystem
- Applying green energy tax policies to improve cybersecurity