phishing

What keeps phishing training from fading over time
When employees stop falling for phishing emails, it is rarely luck. A new study shows that steady, mandatory phishing training can cut risky behavior over time. After one year …

Researchers expose large-scale YouTube malware distribution network
Check Point researchers have uncovered, mapped and helped set back a stealthy, large-scale malware distribution operation on YouTube they dubbed the “YouTube Ghost …

Researchers uncover ClickFix-themed phishing kit
Palo Alto Networks researchers have discovered and analyzed “IUAM ClickFix Generator”, a phishing kit that allows less skilled attackers to infect unsuspecting …

Microsoft spots LLM-obfuscated phishing attack
Cybercriminals are increasingly using AI-powered tools and (malicious) large language models to create convincing, error-free emails, deepfakes, online personas, …

Microsoft disrupts the RaccoonO365 Phishing-as-a-Service operation, names alleged leader
Microsoft and Cloudflare have disrupted a Phishing-as-a-Service operation selling the RaccoonO365 kit for stealing Microsoft 365 account credentials. “Using a court …

Old file types, new tricks: Attackers turn everyday files into weapons
Attackers are finding new ways to blend in with everyday business tools, hiding their activity inside formats and processes that workers and IT teams often trust. The latest …

Fake npm 2FA reset email led to compromise of popular code packages
Malicious versions of at least 18 widely used npm packages were uploaded to the npm Registry on Monday, following the compromise of their maintainer’s account. …

Attackers use “Contact Us” forms and fake NDAs to phish industrial manufacturing firms
A recently uncovered phishing campaign – carefully designed to bypass security defenses and avoid detection by its intended victims – is targeting firms in …
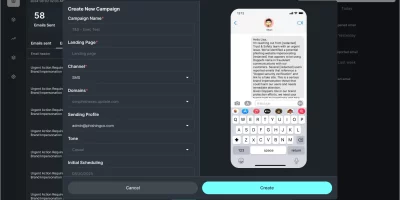
What CISOs can learn from Doppel’s new AI-driven social engineering simulation
Doppel has introduced a new product called Doppel Simulation, which expands its platform for defending against social engineering. The tool uses autonomous AI agents to create …

URL-based threats become a go-to tactic for cybercriminals
Cybercriminals are using advanced social engineering and AI-generated content to make malicious URLs difficult for users to identify, according to Proofpoint. Whether through …

Cybercriminals are getting personal, and it’s working
Cybercriminals are deploying unidentifiable phishing kits (58% of phishing sites) to propagate malicious campaigns at scale, indicating a trend towards custom-made or …

Phishing campaign targets U.S. Department of Education’s G5 portal
A new phishing campaign is targeting users of the U.S. Department of Education’s G5 portal, a site used by educational institutions and vendors to manage grants and federal …
Featured news
Resources
Don't miss
- Initial access broker pleads guilty to selling access to 50 corporate networks
- Confusion and fear send people to Reddit for cybersecurity advice
- Product showcase: PrivacyHawk for iOS helps users track and remove personal data from data brokers
- Fake browser crash alerts turn Chrome extension into enterprise backdoor
- Law enforcement tracks ransomware group blamed for massive financial losses