How to leverage intelligent deception to detect cyber attacks
 Perimeters are fading, and attackers find it easier and easier to penetrate organizational networks. Organizational networks today are chaotic, they’re very dynamic, and this is a fertile ground for the attackers to blend in and take action.
Perimeters are fading, and attackers find it easier and easier to penetrate organizational networks. Organizational networks today are chaotic, they’re very dynamic, and this is a fertile ground for the attackers to blend in and take action.
In this podcast recorded at RSA Conference 2017, Yoel Knoll, VP of Marketing for TopSpin Security, talks about how you can leverage intelligent deception in order to detect cyber attacks.
Here’s a transcript of the podcast for your convenience.
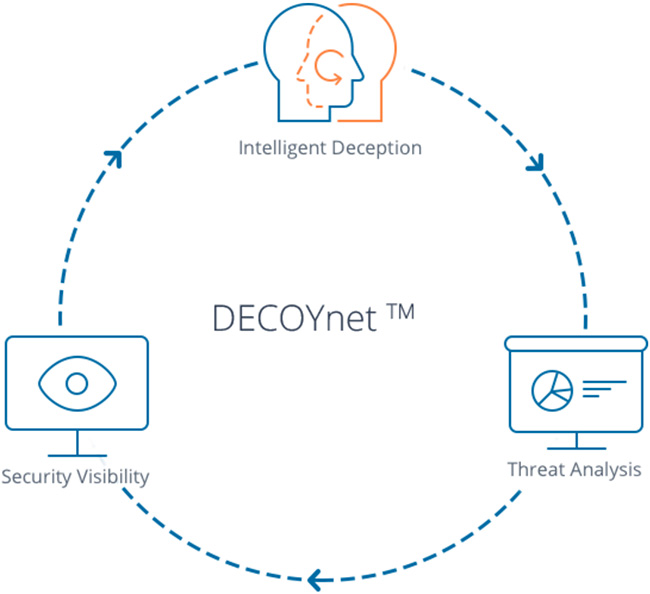
TopSpin Security provides customers with a rapid post-breach detection solution that enables them to actually detect the attacks in their early phase, before the attackers can actually do anything. They do this by combining three engines. First of all, there’s traffic analysis. The second is intelligence deception. And the third is security visibility.
DECOYnet platform
When we come to our customer, the first thing we do is analyze the traffic. We learn the organization, we understand what kinds of assets the organization has or the type of services, the type of applications, the type of users, the type of networks that the organization has. We build a comprehensive map of the organization, and we profile each and every asset.
This information helps us to set intelligent deception AI using decoys, which actually are fake assets that mirror and mimic the organizational assets, and we understand where they need to be placed in order to look just like any other asset in the network so when an attacker looks at it, the attacker cannot tell if this is a real asset or a trap.
The second thing we do is we set lures or breadcrumbs on real assets which point to the decoys. This could be anything from recently deleted files, registry key, fake information and fake data that would lure the attacker and point to the trap.
The last thing we do is we provide security visibility, which actually gives a graphic of you, of how the network looks like, what assets are compromised, and a full story of the attack, of course, once we detect an attack.
Now, this is not just a static type of defense. We know that organizational networks are dynamic, therefore our solution is also dynamic and adaptive. Because we constantly monitor network traffic, we understand changes in the network. We can detect any change in the network from new subnets being raised when you upgrade your OS, when you add new machines et cetera. And then, we can adapt the deception layer to actually mirror or mimic the current structure of the network. And we do this, of course, on an ongoing basis, so this is a very living and breathing deception environment.

DECOYnet dashboard
Protect IoT devices
Recently, we launched the third generation of our DECOYnet platform. And one of the major advancements that we added is the ability to also protect IoT devices within the organization.
Many organizations are adding IoT devices, and it could be anything from a printer to a webcam, VoIP, Voice over IP devices, control systems, routers, switches, central cooling and heating, anything in the organization that has an IP address is basically an IoT and adds to your attack surface. And because these IoT devices have very minimal computing resources, it makes it impossible to use endpoint securities such as antivirus or encryption and other forms of protection in order to actually keep these devices safe. On the other hand, we’re all using them more and more. So, what do you do?
What we offer is a network-based coverage of IoT. Because we can analyze the network traffic, we can recognize IoT assets, and we build and we set up decoys that look and act like an IoT device. So we can, for example, mimic a security camera, a webcam, or we can mimic a printer – going all the way to point of sales systems, medical devices, etc.
We do not put protection on the device itself, but we do create fake devices for the attackers to find. And of course, once they find it and penetrate it, it’s game over for them, because they’ve been detected. And then, we can, of course, call the remediation teams and resolve the threat.
For additional information, you can download a case study with First Midwest Bank.

