How to close the security update gap
Security patching is hard and patch fatigue is real. So what can be done to make the process more simple, less disruptive, and more likely to be performed in a timely manner?
According to the results of a recent survey by ACROS Security, those responsable for it are asking for – among other things – the capability to quickly un-apply patches if they cause problems, security and functional patches to be decoupled, want to have better control over which patches we want to apply, and have the ability to install security patches for all products from one central management point.

“In addition to answering survey questions respondents commented: mobile devices are often out of network, equipment is switched off and all this can delay patch deployment. They prefer just the change of code bits, not entire libraries. They appreciate having complete and frank information on the patch from software vendor (‘if it adds telemetry don‘t call it a fix’, said one of them). Participants also expressed the need for better vendor support for security patching,” the company noted in the report.
Reasons for the security update gap
Lack of money or security awareness turns out not to be among the main reasons for neglecting security patches. The main reasons for the security update gap are:
- “Software updates could break production systems that are working just fine.”
- “Applying patches disturbs our daily business processes.”
- “We can’t afford downtime caused by rebooting our critical systems.”
- “We don’t want functionality changes that come with security patches.”
- “We have to perform extensive acceptance tests.”
58 percent of the 340 polled IT admins, specialists, managers, C-level managers, programming specialists and other professionals say that they have legacy systems working on unsupported platforms that would be expensive to update or replace, and 57 percent of them have applications that are only compatible with old version(s) of operating systems or applications.
“Banking, travel, public sector and other traditional industries are conservative in changing stable platforms and well tested processes. It just has to make business sense to replace a key software framework with a newer version,” ACROS Security points out.
“Due to possible incompatibilities between installed applications the respondents are reluctant to upgrade one or all of them in order to avoid future inconsistencies. So why fix it if it isn‘t broken?”
Nearly a quarter of the pollees also admitted that their sysadmins are not familiar enough with their older systems to apply any changes.
“In addition to answering survey questions respondents commented that they have hard time patching legacy software because of bad architectural or design decisions made in the past. They also said that they don‘t have adequate validation and smoke tests for critical applications and that patching results are not verified by stakeholders,” the company noted.
The respondents put some of the blame for the difficulties they encounter when applying patches on the vendors and their relationship with them. The problems include:
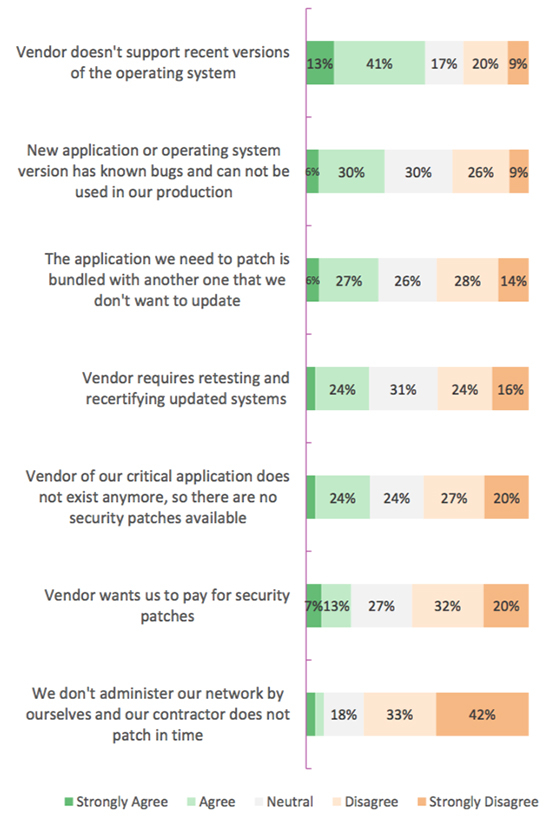
The survey was inspired by security-aware individuals that opened the debate of their patch fatigue after the Equifax attack and, although the respondents are mainly from North American and European countries, the company believes that the results offer helpful insights into the problem.