Telecom services: Patient zero for email-based attacks?
Organizations offering telecommunication services are seeing more advanced malware threats than organizations in other industries, Lastline researchers have found.

They have come to that conclusion after having analyzed all the threats seen by the telecom services companies over the past 30 days and the latest 100 malware samples submitted by Lastline customers in this vertical, and comparing them to the latest global “malscape” statistics.
Unknown/unclassified threats
“Around 90 percent of files [we analyzed] had not been submitted previously to VirusTotal for analysis, which is a significant deviation from the global average of 65% and the polar opposite of the finance sector sitting at around 20%,” the researchers shared.
“This delta could be explained by the implementation of state of the art email security controls in telecom services companies that have necessitated that the threat actors, in order to penetrate defenses, constantly evolve their attacks creating a perpetual Day0 campaign of rotating file types, exploits, and social engineering schemas. The telecom services vertical could well be patient zero for email based attacks.”
As an added risk, the majority of those files that had been submitted to VirusTotal had only generic detections.
“The typical incident response guidance from tools that identify files with these generic descriptions is to restore the device from a known good backup or simply perform a clean re-image. The issue with providing generic guidance is that it does not address the very significant threat posed by malware that is designed to steal credentials, for example,” they explained.
Advanced malware
One in ten malware threats lobbed at telecom services shows advanced behaviours: packers are used to bypass static analysis, evasion behaviors to avoid detection by dynamic analysis systems, stealth behavior (masquerading as or injecting trusted file systems), and the malware is capable of stealing data (credentials) and surveilling user activity. The global average is one in 12.
The researchers believe that might be because the sector’s defenses are more effective and therefore attackers need to deploy more sophisticated threats to be successful.
“Additionally stolen telecom sector credentials play a pivotal role in many forms of cybercrime activities and so threats with steal behaviors play a increased role,” they added.
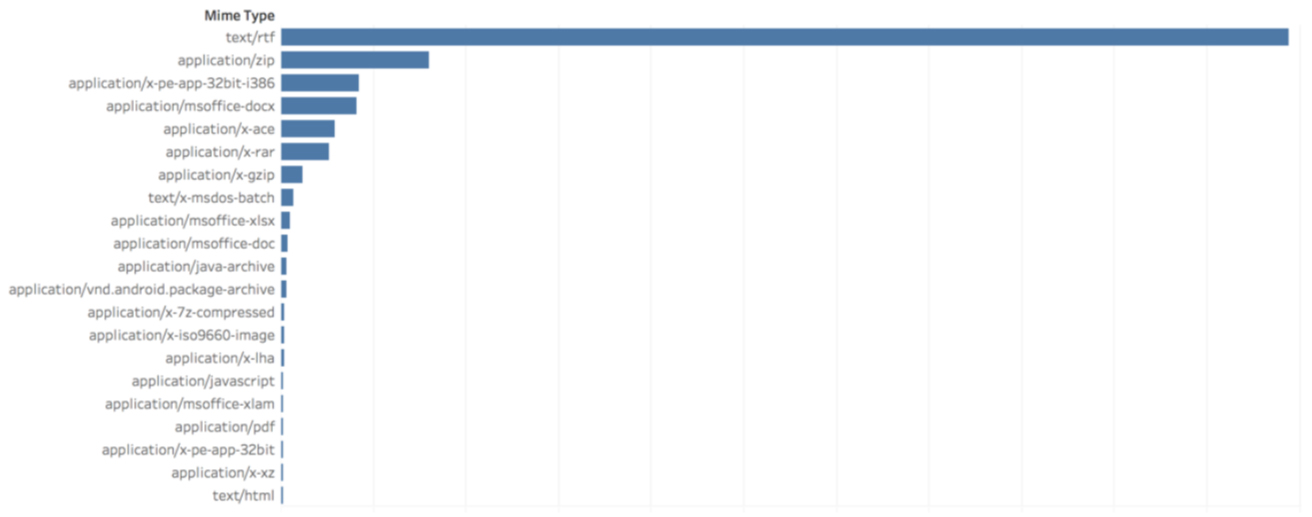
Finally (and curiously), within this sector only 15 file types were used to deliver malware, which is much lower than the global average (40 file types).
In the majority of cases, the malware masquerades as a Rich Text Format (RTF) document, but archive file types are also a frequent choice.
The researchers put it down to the fact that providing email services is one of the key business functions for this sector, and the threat is tailored to email as the vector of compromise.
“Services organisations are ahead of the curve, essentially a Day0 attack, with very few prior submissions of samples being evidenced on VirusTotal. These malspam attacks represent the tip of emerging campaigns and reflect the inherent criminal value in stolen email credentials,” they concluded.