Safe IT/OT integration with unidirectional security gateways

The reason SCADA security is so controversial stems primarily from the intense consequences that come from a compromise in this area. In this podcast, Andrew Ginter, VP of Industrial Security at Waterfall Security Solutions, and Edward Amoroso, CEO of TAG Cyber, talk about how unidirectional security gateways enable safe IT/OT integration.
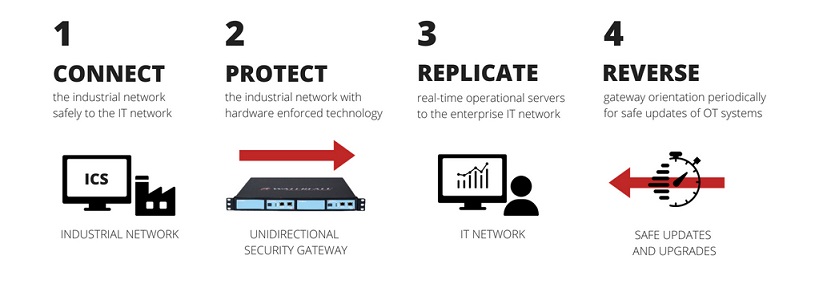
The gateways replace firewalls in industrial network environments, providing absolute protection to control systems and operations networks from attacks originating on external networks. They enable vendor monitoring, industrial cloud services, and visibility into operations for modern enterprises and customers.
Unidirectional security gateways replicate servers, emulate industrial devices and translate industrial data to cloud formats. As a result, unidirectional gateway technology represents a plug-and-play replacement for firewalls, without the vulnerabilities and maintenance issues that always accompany firewall deployments.
Here’s a transcript of the podcast for your convenience.
Andrew Ginter: Hello everyone. This is Andrew Ginter with Waterfall Security, I’m the VP of industrial security there, thank you for joining us. I’m joined on this podcast with Edward Amoroso, the CEO of TAG Cyber and the former CSO at AT&T. Hello Ed.
Edward Amoroso: Hi Andrew.
Andrew Ginter: Thanks for joining us. Today’s topic, we put together a series on industrial control system cybersecurity. Today’s topic is unidirectional gateways. This is something that I’m guessing was new to you when you came to this topic. Can you talk about you know, you being introduced to the gateways.

Edward Amoroso: Absolutely. You know, there are a few basic primitives, principles that haven’t changed much in cybersecurity or computer security since 30, 40 years ago. One of them is separation. If you’ve got two entities and can control how to interact and you separate them, that’s one of the most basic concepts, but it’s easier said than done. I mean, you say that but how do you do it and people have been trying for years to come up with good effective means for separating one domain or network or system from another, or set of actors.
So, I first sort of happened on the unidirectional gateway concept. I got very excited because I think it’s a very effective, almost provable way to create separation where that’s an imperative requirement, and maybe you can take a couple minutes and share how you guys implement that at Waterfall. I think it’s a very elegant design and probably worth taking a couple minutes to summarize.
Andrew Ginter: The unidirectional gateway is a device that fits into a network in the same place as most people, most of the time, would think to deploy a firewall. The issue on control system networks and especially safety critical networks or reliability critical networks – the issue is that firewalls are software, all software has bugs, all software can be hacked, firewalls included, and this is considered an unacceptable risk.
The unidirectional gateway is, you know there is some software involved but it is also hardware involved. Think two boxes – the most popular packaging is sort of all-in-one – but think two boxes. Think the box on the control system that has a transmitter in, a fiber optic laser and a box on the enterprise network that has a fiber optic receiver, a photocell, and there’s a short piece of fiber between these two boxes.
We can gather information with the one box from the control system network. We can push that out to the enterprise network through the one-way hardware and on the enterprise network publish it to whoever needs it, and the essence here is that the control system box has no photocell in it. The circuit board has no fiber optic receiver in it. The circuit board on the enterprise network has no laser. It’s not physically possible to send any signal back into the control system, and so what we have is the ability to monitor in real time the control system without risk: it’s not possible to send anything back.
Edward Amoroso: So, one of the more interesting parts about that design, Andrew, is that it’s almost provable in a sense, right, the physics lend well to demonstration that a one-way policy is implemented. I really like that. I think for high-assurance environments, which means any ICS certainly, but maybe even in a classic IT environment you see assurance requirements that at times can approach the same level of potential consequence that a one way function is a very useful complement.
I know you guys in many cases will say just it’s a flat-out replacement for the firewall and for an awful lot of applications I would concur. So, I hope people take a look at it. We try to summarize the design in our article and I think it’s a good light technical intro, there’s something a little more complex and they’ll have to go to your website to get more design information on how it would be implemented in their network.
Andrew Ginter: The software in the solution is essential to replacing the firewall. You know, the classic design when we’re monitoring industrial operations from an IT network is to have a database in the industrial network gather information from the network and make it available to users on the IT network through a firewall, and the users on the IT network query the database and get their answers back. And if we want to make this a plug-and-play replacement for the firewall, we need to support that mode of interaction and the way we do that with software. On the control system side is a client of that database pulls as much of the data out of the database as we care to publish into the IT network. The software on the receiving side inserts the data into an identical database, and now anybody on the IT network who needs the data queries the IT replica database – not the original. The original is safe behind the hardware, all of the users on the enterprise network who are users and applications who used to query the sensitive database are now querying a replica, and doing so safely because there’s physically no signal being sent back into the control system.
Edward Amoroso: It’s a very clever design and I think anybody listening who digs in will be very pleased with the way it provides extremely high assurance separation. I certainly enjoyed learning how the design was put in place.
Andrew Ginter: And there was a second device we talked about in the article and that is a Flip, and the Flip recognizes that while some industrial processes are monitor-only, there is frequently a need to signal, to trickle some kind of information back into the control system. You know, think antivirus updates need to go in a couple of times a day, or in a refinery or even in mining a lot of physical processes are what are called batch processes, and you produce things in batches, and so the batch production orders saying, you know which raw materials to use, what quality of finished goods to produce, how much of each is involved, these sort of high-level orders saying, “Here, produce this next,” need to trickle back in as well.
And so the Flip is a kind of unidirectional gateway, it’s a different piece of hardware but it has a unidirectional gateway inside it. It can physically send information in only one direction, but there’s a timer inside and when the timer trips it is as if the Flip physically picks up, flips over, and sets down.
It can be one-way-out or one-way-in, but never both, and so when it’s one-way-in, the software can say, “Oh look, here’s my chance.” And, again, the software is not a router like a firewall. None of the unidirectional gateway stuff forwards network traffic. The software’s a client going out and fetching the antivirus signatures, fetching the batch production orders, checking them, you know, crypto signatures and such, pushing through the one-way hardware, and on the other side the software again is a client and checks everything again, and pushes it to where it belongs in the control system, and then the whole thing flips back, typically a couple of minutes later.
So, it’s a disciplined way to send information into a control system. We don’t just open a port on a firewall and cross our fingers and hope for the best. We deliberately send only certain information into the control system.
Edward Amoroso: Yeah. That Flip function allows you to expand the application base considerably. There’ll be a lot of people without the Flip capability who’d say, “Well, I have these special case considerations that wouldn’t be covered.” Having that design element, I think, really does expand the applicability. I hope people take the time to go in and dig into how it works.
Andrew Ginter: Very much so. We certainly do see a steadily increasing number of sites that has made the switch to this technology. They typically deploy one layer of this technology, replacing a layer of firewalls in a defense-in-depth layers of firewalls model, and having deployed the technology at one layer, they break the chain of infection from the Internet into the most sensitive systems.