Hackers using hidden mobile apps and unique distribution methods to target consumers
Hackers are using hidden mobile apps, third-party login and counterfeit gaming videos to target consumers, according to McAfee.
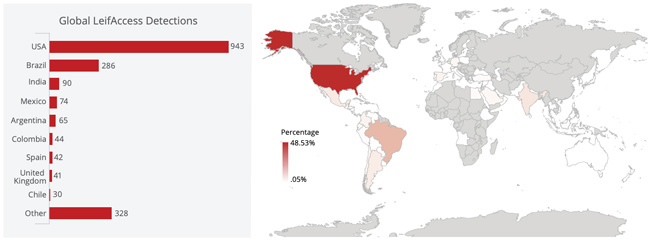
Worldwide detections of LeifAccess, 2019
Last year, hackers targeted consumers with a wide variety of methods, from backdoors to mining cryptocurrencies. Hackers have expanded the ways of hiding their attacks, making them increasingly difficult to identify and remove, which makes it seem like 2020 will be the year of mobile sneak attacks.
Hidden apps: The most active mobile threat
Hidden apps are the most active mobile threat facing consumers, generating nearly 50% of all malicious activities in 2019- a 30% increase from 2018. Hackers continue to target consumers through channels that they spend the most time on- their devices, as the average person globally is expected to own 15 connected devices by 2030.
Hidden apps take advantage of unsuspecting consumers in multiple ways, including taking advantage of consumers using third-party login services or serving unwanted ads.
“Consumers are connected more than ever, and as we look at the current security landscape, as well as future risks, we want to make sure we are doing everything to help consumers protect what matters more to them- their personal data, as well as their family and friends,” said Terry Hicks, Executive Vice President, Consumer Business Group at McAfee.
“Mobile threats are playing a game of hide and steal, and we will continue to empower consumers to safeguard their most valued assets and data.”
Hackers use gaming popularity to spoof consumers
Hackers are taking advantage of the popularity of gaming by distributing their malicious apps via links in popular gamer chat apps and cheat videos by creating their own content containing links to fake apps. These apps masquerade as genuine with icons that closely mimic those of the real apps but serve unwanted ads and collect user data.
Researchers uncovered that popular apps like FaceApp, Spotify, and Call of Duty all have fake versions trying to prey on unsuspecting consumers, especially younger users.
New mobile malware uses third-party sign-on to cheat app ranking systems
Researchers have uncovered new information on mobile malware dubbed LeifAccess, also known as Shopper. This malware takes advantage of the accessibility features in Android to create accounts, download apps, and post reviews using names and emails configured on the victim’s device.
Researchers observed apps based on LeifAccess being distributed via social media, gaming platforms, malvertising, and gamer chat apps. Fake warnings are used to get the user to activate accessibility services, enabling the full range of the malware’s capabilities.
Unique approach to steal sensitive data through legitimate transit app
A series of South Korean transit apps, were compromised with a fake library and plugin that could exfiltrate confidential files, called MalBus. The attack was hidden in a legitimate South Korean transit app by hacking the original developer’s Google Play account.
The series provides a range of information for each region of South Korea, such as bus stop locations, route maps, and schedule times for more than 5 years. MalBus represents a different attack method as hackers went after the account of a legitimate developer of a popular app with a solid reputation.
“There exists a growing trend for many apps to remain hidden, stealing precious resources and important data from the device that acts as the remote control to consumers digital world,” said Raj Samani, McAfee Fellow and Chief Scientist.
“Now, more than ever, it is critical consumers make themselves aware of modern threats and the steps they can take to defend themselves against them, such as staying on legitimate app stores and reading reviews carefully.”