Review: Specops Password Policy
Specops Password Policy is a powerful tool for overcoming the limitations of the default password policies present in Microsoft Active Directory environments. To be fair, Microsoft did revise and upgrade the default password policy and introduced additional, granular fine-tuning options over the years, but for some enterprise environments that’s still not enough, so Specops Password Policy to the rescue!
Installation
For the purpose of this review, the installation was done on a server containing all necessary services: Specops Sentinel – a password filter that is installed on all domain controllers, and Specops Password Policy admin tools. Keep in mind that this can be split onto different servers if needed. If you purchased Breached Password Protection, you’ll need to install Specops Arbiter as well.
The setup process is smooth, and you can expect to be up and running within the hour. As you can see from the image below, the standard requirements are modest and should not be a problem for any enterprise environment that requires such a solution.

Figure 1. Specops Password Policy minimum requirements
Password policy templates
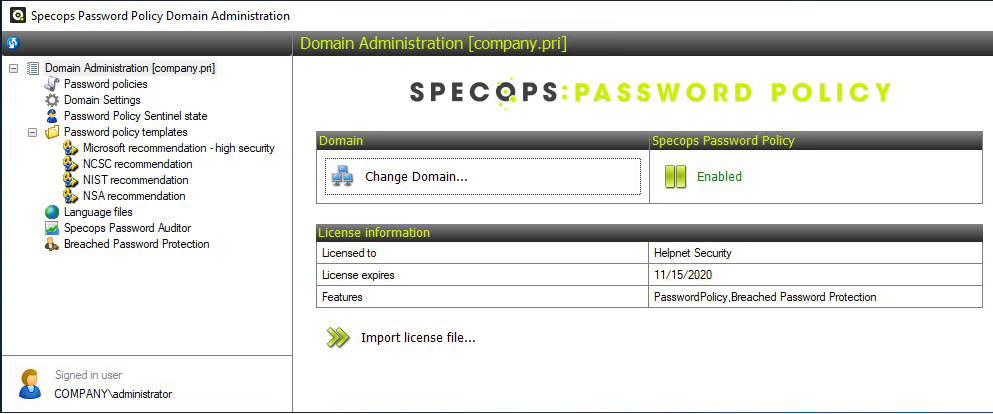
When you start with Specops Password Policy Domain Administration, you’ll notice four predefined password policy templates you can choose from:
Figure 2. Specops Password Policy Domain Administration including default templates
These templates are convenient for a fast setup but, naturally, you can take them to another level by customizing them. If you’re working in an environment that needs to meet specific regulatory standards, the provided templates can be a lifesaver. Even if you can’t or don’t want to use these policies, you can use them as a base to strengthen your policy or create a policy compatible with your environment.
Let’s create a new, blank policy to see what the process looks like. Creating one will take you to the Group Policy editor:
Figure 3. Specops Password Policy inside the Group Policy editor
If you find it familiar, it’s because it is the same environment where you would change your default password policy inside Active Directory. The one key difference here is that Specops Password Policy applies password settings to the user part of group policy rather than computer. This makes more sense as it’s the users that generally set bad passwords rather than machines.
After testing the options and thinking how this would fit into my network, I have to commend Specops for not unnecessarily complicating things and choosing to go with a workflow most system administrators are familiar with.
Passphrases
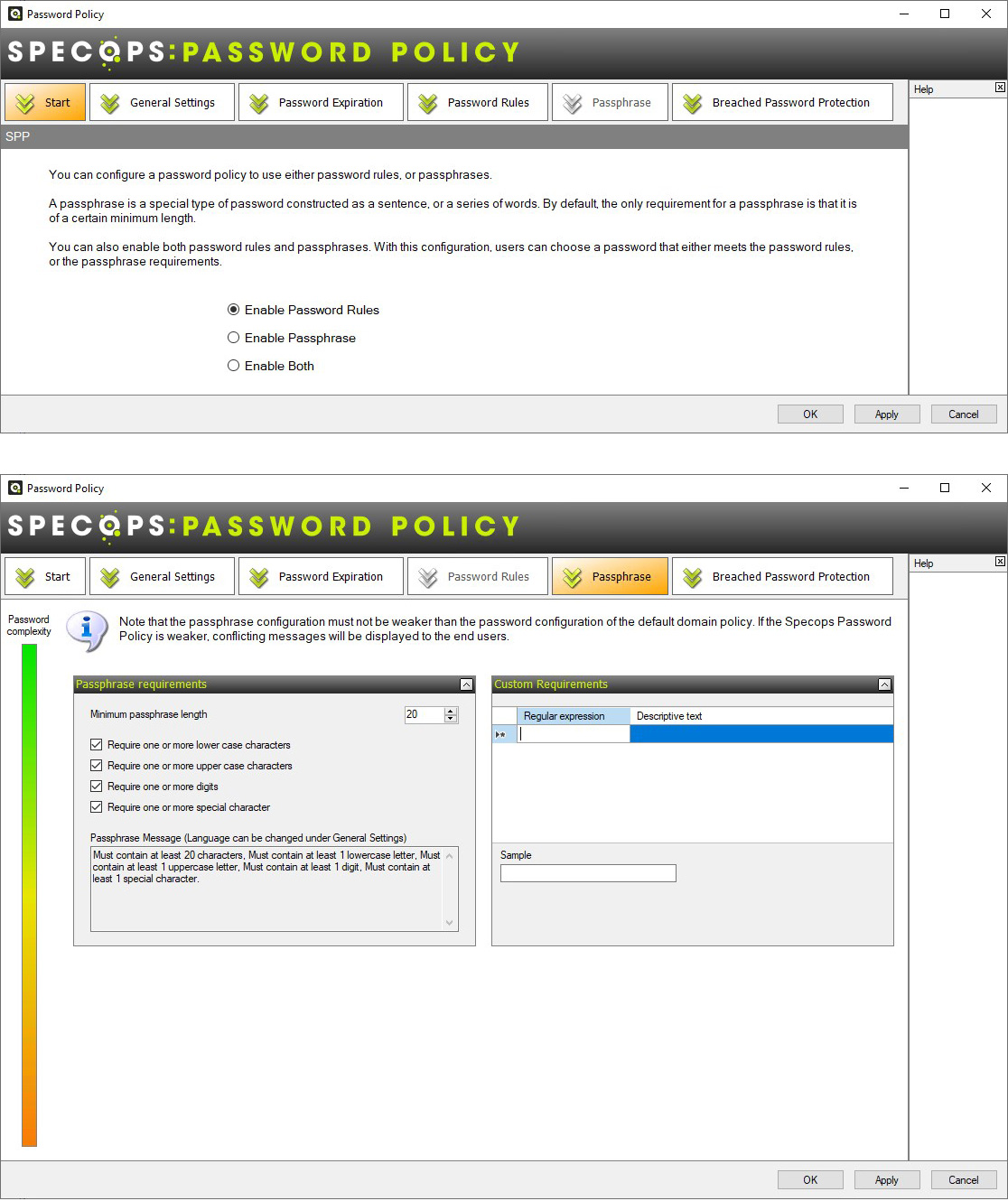
When I opened Specops Password Policy inside the Group Policy editor, I was pleasantly surprised to see that it supports the use of passphrases. More importantly, it also offers assistance for handling them (something that Active Directory does not). You can use regular expressions so that you can define what a passphrase means to your organization i.e. 3 words, with at least 6 characters in each word, no words should be repeated, and no patterns should be used 111111 222222 etc.
Figure 4, 5. Passphrase support and password options
The General Settings menu offers familiar settings for anyone that’s used to working with the Group Policy Editor in an Active Directory environment. A neat addition here is the “client message” option, which allows you to create a custom message to be shown on the Active Directory logon screen in case the password policy requirements are not met.
Figure 6. General Settings with options and client message notification
Password options
The Password Expiration tab offers a wealth of options, including the maximum password age, password expiration notifications, and so on. A key feature here is the length-based password aging rule. This means that the longer the password the longer the user gets to keep it. It can be real incentive to encourage users to move to passphrases.
Figure 7. Options for password expiration rules and password expiration notifications
The Password Rules menu brings additional password rules granularity which should allow for virtually any password policy scenario. Worth noting is that the use of dictionaries with forbidden words is possible either by creating a custom dictionary or downloading dictionaries provided by Specops.
Figure 8. Regulating password rules requirements in one place
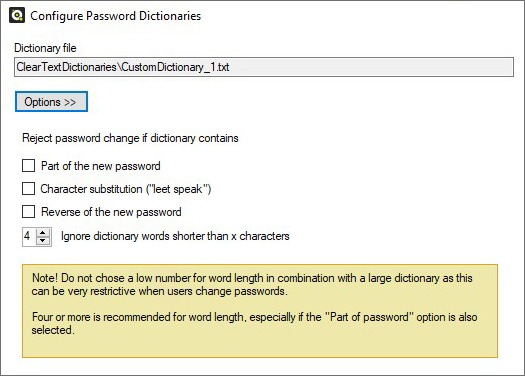
Figure 9. Additional protection from users trying to subvert the password policy
Breached Password Protection
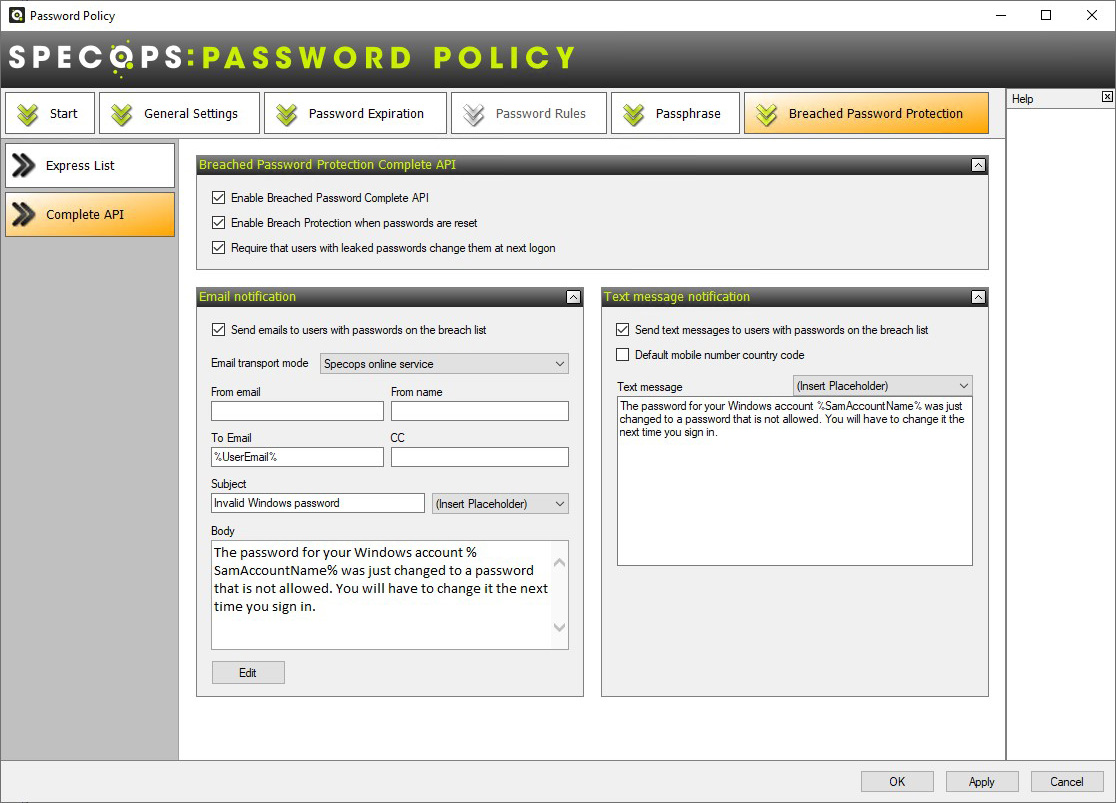
A great set of options are found under Breached Password Protection. In a nutshell, it allows the system to compare an Active Directory password to a list of known breached passwords. As might be expected, passwords are hashed in the process.
If a password is discovered in the breached password list, the action triggers the delivery of notifications/alerts.
Figure 10. Breached Password Protection Complete API
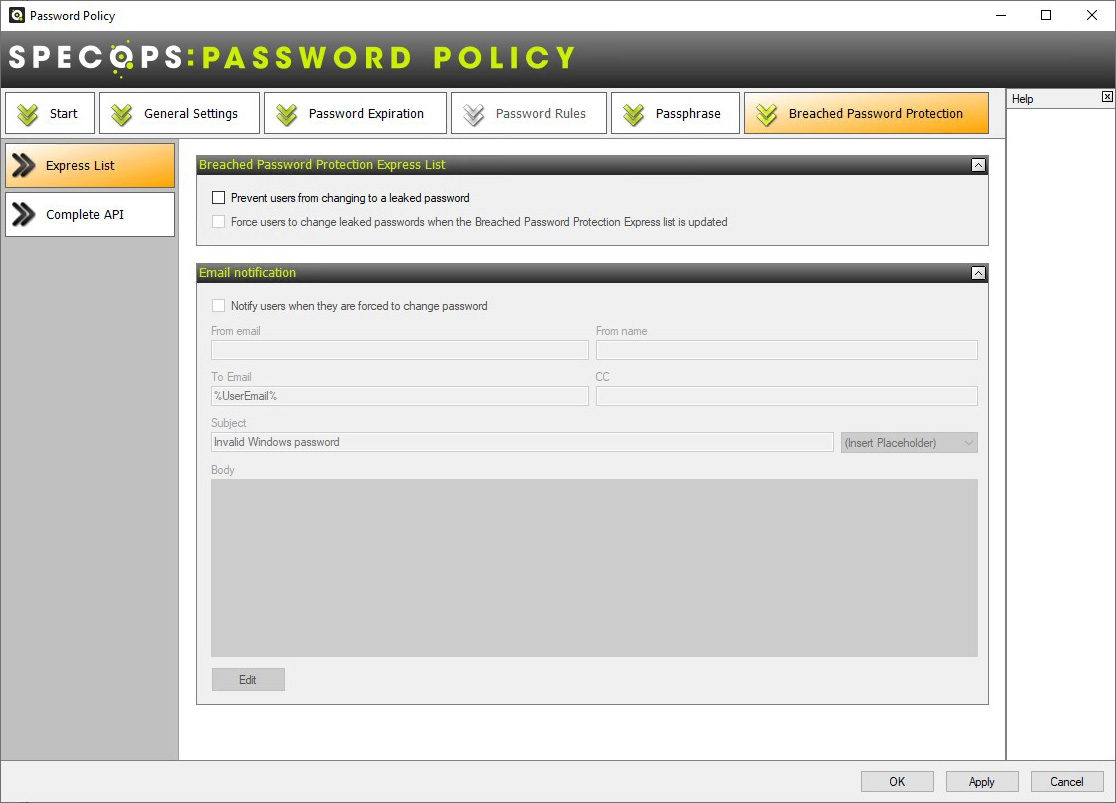
Figure 11. Breached Password Protection Express List
With the API, Specops Password Policy supports both email and SMS notifications. When using the Express List (a downloadable passwords list) you can use only email notifications.
I realize there’s a narrow application for it, but I would like to see support for custom SMS gateways in future versions, as large enterprises might find this useful. Specops Software tells me that since there’s no extra cost involved for using the SMS notification feature they’ve never been asked to provide a custom SMS platform.
What’s new?
The latest version of Specops Password Policy comes with several powerful new features, Powershell CMDlets and a security scanner.
Leaked password scanning
While Powershell support is nothing new to Specops Password Policy, the latest version brings us powerful new CMDlets:
- Get-SppPasswordExpiration and Get-PasswordPolicyAffectingUser are user-related CMDlets enabling checks which until now could not be requested nor scripted trough Powershell. I found them rather useful during troubleshooting while trying to discern why a certain policy was not working as intended. Using CMDlets with pretty self-explanatory names is much faster than going through the menus of a newly installed application.
- Get-SppPasswordExpiration checks for the password expiration date, returning the date and reliability of the password.
- Get-PasswordPolicyAffectingUser – if you ever handled a multi-policy environment, you know that something simple as knowing the exact policies applied to the user can be the difference between solving an issue or entering a virtually endless troubleshooting loop. You just need to provide the username in sAMAccountName or userPrincipalName format for which the CMDlet returns GpoID, GpoName, and the password policy name.
- Start-PasswordPolicyLeakedPasswordScanning – As evident from the name, it starts scanning for leaked passwords in your Active Directory environment. Even though this feature is present in the Domain Admin tool, this CMDlet is useful as it can be scripted and delayed, which is ideal for administrators working in large environments. After running the CMDlet, all users that are non-compliant to the policy will be notified on the next logon to change their password. Leaked passwords scanning requires the Specops Breached Password Protection license.

Figure 12. All available Specops Password Policy CMDlets
Looking after your passwords
Specops Software maintains a comprehensive list of leaked passwords based on numerous sources. It contains billions of passwords and is often updated.
Breached Password Protection can be configured with two settings: Breached Password Protection Complete and Breached Password Protection Express.
The Complete setting comes with a master list of leaked passwords that are stored in the cloud. If a user changes their password to one that can be found on the list, a notification is sent via email or SMS, and they are forced to change their password the next time they log in. For this, you’ll need .Net 4.7.1 and Windows Server 2012 R2 or later, with an installation of Specops Arbiter and an API key.
Breached Password Protection Express downloads a subset of the list of leaked passwords, updated usually every 6 months. This also means administrators will need to manually check for updates and initiate a download of the updated list. Users are also immediately prevented from changing their password to a password found in the leaked list.
Length based password expiration
Specops has found a way to reward security-conscious users by extending the timeframe for mandated password change.
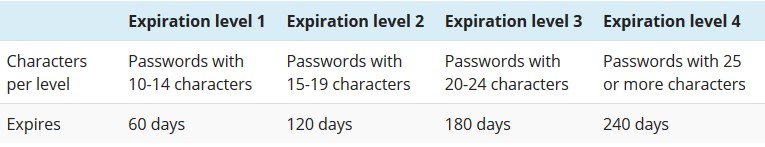
Figure 13. The longer the password, the later it expires
Users can be notified of their upcoming mandated password change. As the timeframe for mandated password change is dictated by password length, notifying users is of great importance as it can help user to prepare in advance. The notification can be shown to the users using regular Active Directory resources, on the logon screen or via email. For both methods you can define the number of days before a mandated password change notification is shown or sent.
Password Auditor
This is a security scanner for Active Directory, and it’s such a simple yet invaluable tool. It is included in Specops Password Policy and is available as standalone freeware. It groups all possible password security issues found inside your Active Directory. This at-a-glance overview essentially points out all the things you need to worry about, and it’s the place to discover quickly if there’s a problem you might not be aware of like a password being on a leaked list.
Specops has chosen smart way of aggregating important areas around password security and polices, showing the most relevant issues and offering quick insight of potential issues.

Figure 14. A closer look at expiring passwords
Once you’re aware of all the issues, you can quickly focus on what’s critical. I find this to be an easy way to audit your Active Directory environment for a variety of issues at the same time.
Conclusion
After testing Specops Password Policy for a week in a variety of scenarios, I can definitely say we’re talking about a formidable solution. Not only does it make the process of strengthening the password policies better while being simple to use, but it can detect and resolve issues you might not be aware of in the first place.
I can highly recommend Specops Password Policy for any Active Directory environment, and I would go as far as to say it’s a necessity for complex environments dealing with compliance regulations, as well as specific password policy requirements. This solution can raise security level on any Active Directory environment, and you can’t argue about the benefits of better security, can you?