Product showcase: The Intruder vulnerability management platform
Vulnerability scanning is a fundamental component of every good cyber security strategy – but it can be challenging to get right. Intruder created a vulnerability management platform to make it simple and save time, so that every business can enjoy the same level of security as banks and governments worldwide but without the complexity.
Whether you’re just starting out on your cyber security journey or looking to improve existing security controls, Intruder effortlessly finds cyber security weaknesses in your systems to avoid costly data breaches.
What you need to know before diving in
Simple: we want everyone to be secure, so our tool is designed to be as simple to use as possible with clear and actionable results, saving you time and helping you focus on what matters.
Proactive scanning: when new vulnerabilities are discovered, we run proactive emerging threat scans, looking for new weaknesses.
Attack surface reduction: we highlight issues that are important in the context of being exposed to the internet like databases, which are a common cause of security breaches.

Getting started: see how easy it is to use
Add your targets
Manually add targets: simply add your internal targets such as employee laptops or servers behind firewalls (or add them automatically using our set-up wizard) and your external systems by entering the IP addresses/hostnames.

Add from cloud providers: connect your AWS, Google Cloud or Azure accounts to synchronise your external IP addresses and DNS hostnames with the Intruder portal, or create rules to choose exactly what gets pulled in from your cloud account for greater flexibility.

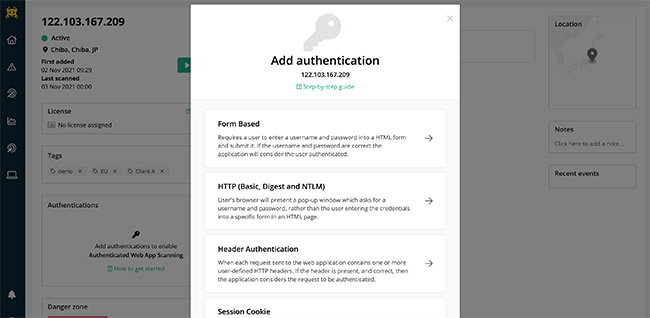
Add authentication: If you want to scan behind the login page, it’s easy to add authentication to the target.
Scans
We run monthly scheduled scans by default, but you can choose to run a scan whenever you want, or create multiple scans to run against whatever tag(s) or target(s) you like.
Once a scan is completed, you can see any issues that we found in your dashboard. Each issue will have a description in user-friendly language for non-security professionals, with more in-depth remediation advice and a list of targets affected. Unlike some scanners, we reduce ‘noise’ so that informational-only findings are deprioritised to save you time.

Integrations
Intruder’s integrations are designed to accelerate your productivity. Use the API to manage targets and kick off scans, or embed Intruder into your dev pipeline for peace of mind. Our cloud connectors integrate with AWS, Google Cloud and Azure, while you can notify your team about issues in Slack or MS Teams, or push them to Jira for remediation.

Reports
Intruder’s reports are easy to read and understand. They include a summary of the checks we’ve carried out, and can be used to show scanning and pentesting are in place for compliance and audits including ISO 27001, SOC 2 and Cyber Essentials.

Cyber hygiene score
New vulnerabilities appear all the time. So even when you’ve fixed them, you might be back to square one after the next scan. That’s why measuring how quickly your team fixes them is as important as the total number of vulnerabilities. Our Cyber Hygiene Score keeps track of how long you take to fix issues, and how you stack up against the industry benchmark.
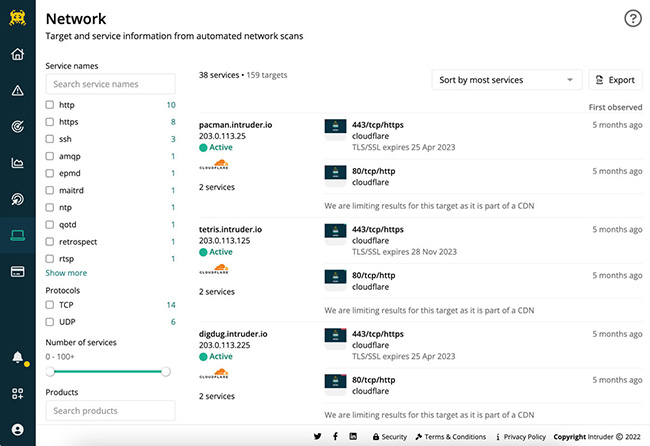
Attack surface management
If you have a large network, it can be difficult to keep up with continuous change. To make it easier, Intruder provides an up-to-date view of your attack surface to help you to:
- Increase visibility: get a clear picture of what’s accessible across your internet-facing infrastructure and easily hunt for services that could expose you to risk
- Preview web assets: identify any web services that don’t belong on the internet, such as exposed infrastructure or application admin panels
- Stay on top of changes: use services like Slack to notify your technical team about important changes to your network as soon as they happen
- React faster: when zero-days are discovered, we help identify your risk and limit your exposure, even when there is no official vulnerability check available
Conclusion
Effective cyber security starts with getting the basics right. Intruder helps you do that, saving time on the easy stuff, so you can focus on the rest. Start your free trial today.