GitHub to introduce mandatory 2FA authentication starting March 13
Starting March 13, GitHub will gradually introduce the 2FA enrollment requirement to groups of developers and administrators, beginning with smaller groups. This measured approach allows the platform to ensure successful onboarding and make necessary adjustments before scaling to larger groups throughout the year.
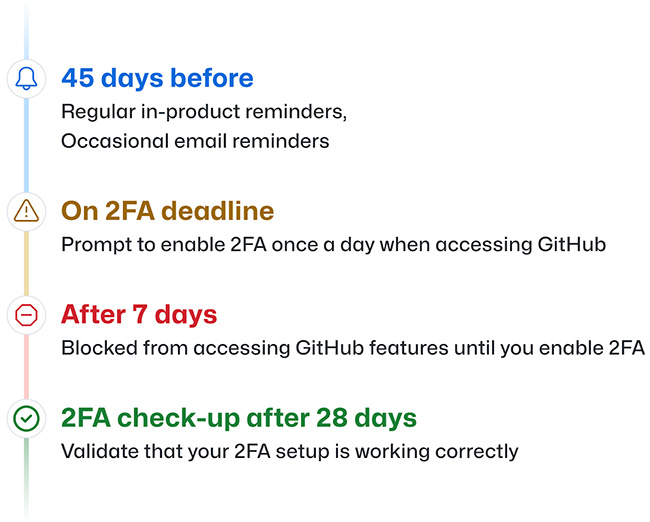
What you can expect
In case your account is selected for enrollment, you will receive a notification via email and see a banner on GitHub.com requesting you to enroll in 2FA. You will have a 45-day window to configure 2FA on your account, and before that date, you can continue to use GitHub as usual except for the occasional reminders. GitHub will notify you as the enablement deadline approaches, and once it has passed, you will be required to enable 2FA the next time you log in to GitHub.com.
You will have the option to snooze the notification for up to a week, but after that, your account access will be limited until you enable 2FA. However, the snooze period will only begin once you sign in after the deadline. If you are on vacation or out of the office, you will still have one week to set up 2FA when you return to your desk.
“We have seen a real trend of attackers targeting private Git repositories through targeted campaigns against developers. 2FA is a welcome step by GitHub that will positively impact code security. However, code is still a leaky asset, and organizations shouldn’t rely on 2FA and instead ensure no sensitive data is stored in Git or code,” Mackenzie Jackson, Developer Advocate at GitGuardian, told Help Net Security.
“Most cloud applications fall into the unmanageable category, meaning they don’t support standards like single sign-on (including GitHub, unless you pay for enterprise), which means passwords will remain with us for much of the decade. While passwords were never the problem, but rather the user’s handling, 2FA remains the gold standard for securing access to digital identities. Kudos to GitHub for moving towards security by default,” Matt Chiodi, Chief Trust Officer at Cerby, opined.
GitHub 2FA highlights
Second-factor validation after 2FA setup
After setting up 2FA, GitHub.com users will receive a prompt 28 days later, requesting them to perform 2FA and confirm their second-factor settings. This prompt helps prevent account lockouts caused by misconfigured authenticator applications (TOTP apps). If you encounter issues performing 2FA, you will be presented with a shortcut that allows you to reset your 2FA setup without getting locked out of your account.
Enroll second factors
Enrolling second factors is essential to ensure you always have access to your GitHub account. You can now register both an authenticator app and an SMS number on your account simultaneously. While security keys and TOTP apps are recommended over SMS, allowing both options reduce the risk of account lockout by providing an accessible and understandable 2FA alternative that developers can enable.
Choose 2FA method
You can choose your preferred 2FA method for account login and use of the sudo prompt. The new preferred option empowers you to select between TOTP, SMS, security keys, or GitHub Mobile as your preferred 2FA method. Although SMS-based 2FA is no longer recommended under NIST 800-63B, it remains a valid 2FA method. However, GitHub advises using security keys and TOTPs wherever possible, as they provide the most robust security.
The most reliable methods currently available support the WebAuthn secure authentication standard. These methods include physical security keys, as well as personal devices that support technologies like Windows Hello or Face ID/Touch ID.
2FA lockout and email
Unlinking your email address from a 2FA-enabled GitHub account is now possible in the event of a lockout. Since GitHub accounts require a unique email address, users who are locked out may struggle to create a new account using their preferred email address – the one linked to all their commits.
With this feature, users can unlink their email address from a two-factor enabled GitHub account if they cannot sign in or recover it. If you cannot recover your account through an SSH key, PAT, or a device previously signed into GitHub, you can create a new GitHub.com account and keep your contribution graph green.