Security teams are carrying more tools with less confidence
Enterprise environments now span multiple clouds, on-premises systems, and a steady flow of new applications. Hybrid and multi-cloud setups are common across large organizations, and they bring a constant stream of logs, alerts, and operational data. That environment already exists across many enterprises, and it frames a recent Sumo Logic study that examined how security leaders manage tooling, staffing, and detection across these systems.
Tooling designed for changing application environments
Security leaders generally describe their current tooling as adequate, yet confidence drops when asked about how well those tools support application environments. Only a minority strongly agree that their security tooling aligns with microservices, containers, and cloud-native architectures. Many teams rely on hybrid SIEM deployments that combine on-premises components with cloud-based analytics, reflecting a gradual shift.
Cloud adoption remains the strongest driver behind changes in security tooling. Application complexity, DevOps acceleration, and governance requirements also influence tooling decisions. These pressures arrive at the same time that application changes accelerate, with most organizations reporting moderate to high rates of change across their environments.
Confidence gaps in SIEM performance
Security leaders express mixed views about the performance of their SIEM platforms. Most say their SIEM contributes to faster detection and response, yet only half describe that contribution as strong. Confidence in long-term scalability follows a similar pattern, with many teams expressing partial confidence as data volumes and monitoring demands continue to grow.
Satisfaction with log management and security analytics tools mirrors this split. Teams that express higher satisfaction also report stronger alignment between their tooling and application environments. These teams tend to rate detection and response capabilities more favorably, suggesting a link between log visibility and operational confidence.
Lean teams and operational strain
Staffing constraints remain a consistent backdrop for security operations. Many organizations operate with smaller teams due to budget limits and hiring challenges. Tooling plays a central role in determining how well these teams can manage alert volumes and investigation workloads.
Fewer than half of security leaders say their current tooling supports lean team structures well. Teams describe partial support, which often translates into manual work, fragmented workflows, and longer investigation cycles. Unified monitoring and security tooling emerges as a widely shared interest, with leaders agreeing that consolidation could improve day-to-day operations.
Automation and AI usage patterns
Automation has become common across detection and response workflows. Most organizations report that key detection and response steps rely on automated processes. AI adoption also appears widespread, though usage concentrates on a narrow set of tasks.
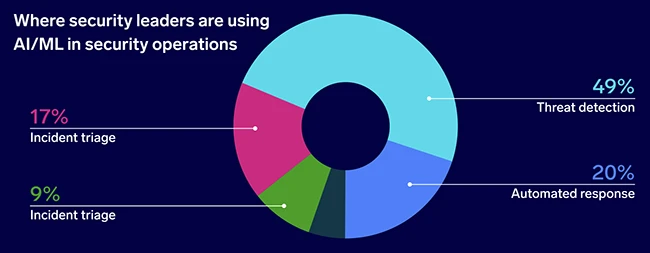
Threat detection represents the most common use of AI and machine learning within security operations. Fewer teams apply AI to incident triage, automated response, or anomaly detection. Despite this limited scope, security leaders consistently associate AI with reduced alert fatigue and improved signal quality. Many also prioritize AI capabilities when evaluating SIEM platforms, alongside real-time analytics.
The weight of tool sprawl
Most security teams operate multiple security operations tools. Three or more tools represent the norm, and many organizations rely on six or more platforms across detection, monitoring, and response. Larger organizations tend to carry heavier tool inventories, though tool sprawl appears across company sizes.
Security leaders frequently describe operational cost as a top pain point. Multiple point solutions contribute to overlapping capabilities, siloed data, and increased alert noise. Data that remains isolated across tools complicates threat analysis and slows investigations, particularly when teams attempt to reconstruct activity across cloud, identity, and application layers.
“Many of the new tools don’t communicate with one another, creating more work and less reliable coverage. The biggest problem we see is security teams becoming leaner, meaning they have even less capacity to connect the dots between siloed tools and actually provide protection to their organization,” said Chas Clawson, VP of Security Strategy at Sumo Logic.
Security and DevOps alignment
Security and DevOps teams often share observability tools, but alignment on workflows and ownership remains uneven. Responsibility for cloud operations tooling varies across IT, security, and DevOps functions. Teams report partial alignment, with fewer describing close coordination.
Organizations that report stronger alignment between security and DevOps also describe higher satisfaction with their tooling and greater confidence in detection and scalability. These teams more often view their tooling as suitable for dynamic application environments, suggesting that shared visibility and workflows influence operational outcomes.