Ransomware groups shift to quadruple extortion to maximize pressure
Threat actors are using a new quadruple extortion tactic in ransomware campaigns, while double extortion remains the most common approach, according to Akamai.
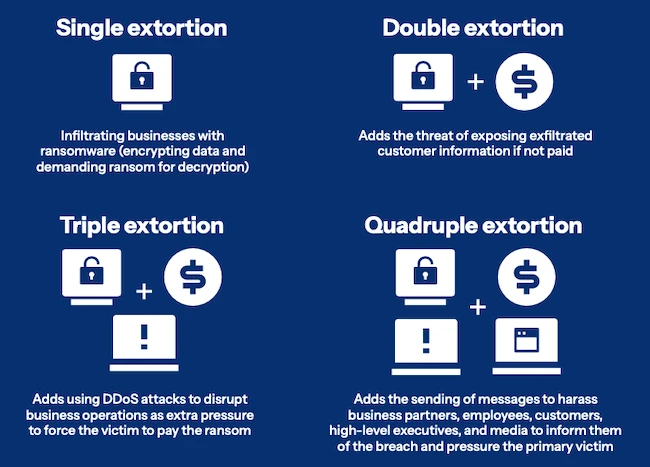
Ransomware extortion tactics (Source: Akamai)
The emerging trend of quadruple extortion includes using DDoS attacks to disrupt business operations and harassing third parties, like customers, partners, and media, to increase the pressure on the victim. It builds on double extortion ransomware in which attackers encrypt a victim’s data and threaten to leak it publicly if the ransom isn’t paid.
“Ransomware threats today aren’t just about encryption anymore,” said Steve Winterfeld, Advisory CISO at Akamai. “Attackers are using stolen data, public exposure, and service outages to increase the pressure on victims. These methods are turning cyberattacks into full-blown business crises, and are forcing companies to rethink how they prepare and respond.”
How attackers are harnessing AI and LLMs
Adversaries are quickly adopting AI and LLMs to make their operations more scalable and sophisticated. Ransomware groups use generative AI to write malicious code, create new ransomware variants, and even deploy chatbots to negotiate with victims. Attackers also use AI to craft realistic phishing emails and carry out vishing attacks that mimic company employees. Some APT groups have also started using generative AI, though on a smaller scale.
Putting the RaaS in hacktivism
Ransomware-as-a-Service (RaaS) has changed how ransomware attacks are carried out. What used to be complex operations requiring advanced skills are now offered as subscription-based services that many more criminals can use. This shift removes the technical barriers that once made ransomware difficult to deploy, allowing even those with little expertise to launch powerful attacks.
By turning ransomware into a service, skilled developers in criminal groups can earn steady income, while less technical criminals can take part in major digital extortion efforts. As a result, RaaS has led to more frequent and widespread attacks, forcing organizations to strengthen their cybersecurity defenses to stay protected.
Hacktivist/ransomware hybrid groups are increasingly using RaaS platforms to amplify their impact, driven by a mix of political, ideological, and financial motives. These groups have evolved from previous hacktivist organizations; for example, Dragon RaaS emerged in 2024 as an offshoot of Stormous, shifting its focus from targeting major corporations to smaller organizations with weaker security.
Cryptominers
Cryptominers, like ransomware, are mainly driven by financial gain through anonymous cryptocurrency transactions. While ransomware usually involves breaking into networks and demanding quick ransom payments, cryptominers quietly use an organization’s computing power to earn steady, low-risk profits over time.
Though they work differently, both cryptominers and ransomware stem from the same motive: making money.
Akamai researchers found that nearly half the cryptomining attacks they analyzed targeted nonprofit and educational organizations, likely because of a lack of resources within these industries.
Ransomware and the law
Ransomware is one of the biggest cybersecurity threats to organizations worldwide. In response, governments have introduced laws, regulations, programs, and awareness campaigns to address it.
Many legal measures aimed at ransomware are based on broader cybersecurity laws rather than being specific to ransomware. Although ransomware is widespread and damaging, it is still treated as one type of cyberattack among many. The same legal standards apply, and following established cybersecurity best practices remains an effective way to reduce the risk.
James A. Casey, VP and Chief Privacy Officer at Akamai, explains that current cybersecurity laws already cover ransomware, but some regulations are aimed specifically at discouraging ransom payments. He points to cybersecurity, incident reporting, and risk management as key elements in protection against ransomware. Strategies such as zero trust and microsegmentation are also important. Casey emphasizes that organizations must stay informed and adjust their defenses as threats evolve.