Weak alerting and slipping prevention raise risk levels for CISOs
Prevention effectiveness is falling, detection gaps remain wide, and attackers are exploiting weaknesses in data protection and credentials. Data theft prevention has dropped to 3 percent, password cracking success rates have nearly doubled, and new threat groups are bypassing defenses.
The latest Blue Report from Picus Security shows that prevention effectiveness against cyberattacks has dropped for the first time in two years, falling from 69% in 2024 to 62% in 2025. Detection capabilities remain weak, with less than one in seven simulated attacks triggering an alert.
Researchers analyzed over 160 million attack simulations conducted between January and June 2025. The findings show that while some areas have improved, key weaknesses remain across industries, regions, and attack types.
Prevention challenges and high-risk gaps
Prevention scores fell in many areas. Data exfiltration prevention, already the lowest-ranked attack vector in previous years, dropped sharply from 9% to just 3%. This decline is occurring as attackers increasingly use double extortion ransomware and infostealers to steal and leak sensitive data.
Dr. Suleyman Ozarslan, VP of Picus Labs, says there are specific steps CISOs can take to close this gap. “In data exfiltration attacks, adversaries usually access sensitive files and then exfiltrate them in bulk. Security teams can use Windows Event ID 4663 to detect access to sensitive data and Sysmon Event ID 3 to track outbound network connections to uncommon destinations or encrypted traffic being sent to external locations,” he explains. By correlating these logs, organizations can quickly identify unusual file access and potential data theft.
Not all exfiltration attempts look the same. Some attackers use legitimate cloud storage or email systems to move stolen data, avoiding suspicious network patterns. Dr. Ozarslan advises configuring DLP tools to identify and block sensitive data transfers unless initiated by an authorized user or application. He also stresses that “implementing these security controls is only the beginning” and recommends regularly validating them with real-world simulations to keep pace with evolving attacker methods.
Password cracking attempts succeeded in 46% of tested environments, nearly doubling from 25% last year. The report points to weak password complexity, outdated hashing algorithms, and inconsistent application of multi-factor authentication as major factors.
Valid Accounts, a MITRE ATT&CK technique where attackers use stolen or weak credentials to gain access, had a prevention rate of only 2%. Discovery techniques like System Network Configuration Discovery and Process Discovery also scored in the low double digits, showing how easily attackers can map out environments without being blocked.
Some areas improved. macOS endpoint prevention rose from 23% to 76%, closing much of the gap with Windows (79%) and Linux (69%). Attack Path Validation testing showed fewer successful domain administrator compromises, dropping from 24% to 19%. Domain admin access fell from 40% to 22%. These gains suggest better lateral movement defenses and network segmentation.
Detection remains a weak link
The log score, which measures whether attacker behaviors are recorded, held steady at 54%. The alert score, which shows how often those events trigger actionable alerts, improved slightly from 12% to 14%. Researchers warn that this gap between logging and alerting leaves many threats undetected.
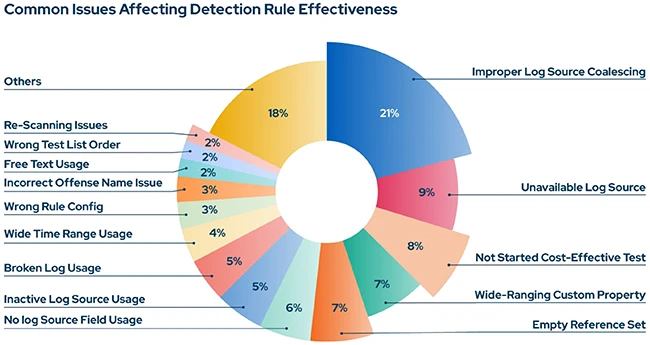
Detection rule failures were most often caused by log collection problems, which accounted for half of all issues. Other failures came from performance problems and misconfigurations. In many cases, rules existed but silently failed to trigger because of integration issues or outdated logic.
Industry detection results varied widely. Government and non-profits achieved the best balance, with a 73% log score and a 50% alert score. By contrast, professional services recorded a 76% log score but only a 5% alert score, showing serious correlation and alerting gaps.
Recommendations for CISOs
Researchers advise moving from simple exposure inventories to adversarial exposure validation, which tests whether exposures can actually be exploited. This approach helps organizations focus on risks that matter rather than on theoretical ones.
Dr. Ozarslan notes that prioritization and validation are core to a successful Continuous Threat Exposure Management (CTEM) program. Instead of aiming for broad ATT&CK coverage, which may cover many techniques but lack relevance to active threats, he recommends focusing on the threat groups most active in a sector and region. This requires using threat intelligence to identify those groups, then refining detection and prevention efforts toward their specific TTPs. “Integrating threat actor profiles into workflows and regularly testing with simulated targeted attacks ensures defenses are informed by real, evolving threat actors instead of hypothetical situations,” he says.
To address the 3% prevention rate for data exfiltration, researchers recommend improving outbound traffic monitoring, deploying and validating DLP rules, and adding behavioral detection for covert data transfers.
On credentials, they suggest enforcing stronger password policies, replacing outdated hashing methods, and regularly testing defenses with simulated cracking attempts.
Given the drop in prevention effectiveness, the report calls for continuous validation and tuning of security controls to counter configuration drift and the impact of evolving threats. On detection, CISOs should ensure telemetry coverage, fine-tune correlation rules, and confirm that alerts are generated and escalated for attacker behaviors.
Ransomware defense recommendations include simulating not only encryption-based attacks but also newer encryptionless extortion tactics to test detection, containment, and response before an incident occurs.
Finally, to improve detection of common techniques like credential abuse and early-stage discovery, researchers recommend using behavioral and identity-aware detection methods instead of relying only on static signatures. They stress the importance of regularly validating controls against common adversary techniques that attackers depend on most.