Ransomware attackers used incorrectly stored recovery codes to disable EDR agents
All target organizations are different, but ransomware attackers are highly adaptive and appreciate – and will exploit – any mistake you make.
The latest Akira ransomware attacks
Managed security service providers and external incident responders have had a front-row seat for observing many of the actions carried out by Akira ransomware affiliates in the last few months.
In early August 2025, both Arctic Wolf and Huntress researchers warned about the possibility of Akira affiliates using a zero-day vulnerability in SonicWall firewalls to perform pre-ransomware intrusions.
A few days later, though, SonicWall said that the attackers are actually still using CVE-2024-40766, a vulnerability that SonicWall had issued patches for in August 2024. The company claimed that some of the targeted organizations might have implemented the fix, but that they had migrated Gen 6 to Gen 7 firewalls without resetting the local user credentials, which had been apparently compromised beforehand.
During the same period, Huntress security experts began sharing tidbits about the attacks they witnessed.
“It is apparent that some of these attackers have at least part of the same playbook, or that they are adaptive to whatever situations they happen to encounter,” they said.
“Methodologies varied from utilizing tools brought in like Advanced_IP_Scanner, WinRAR, and FileZilla, to relying on various built-in tools (LOLBins), as well as installing various persistence mechanisms like new accounts, SSH, or full-blown RMMs like AnyDesk.”
Subsequent reports by other cybersecurity companies pointed out the attackers’ use of:
- Legitimate (but vulnerable) Windows drivers (rwdrv.sys and hlpdrv.sys)
- The -dellog argument to clear event logs
- Built-in Windows tools (Set-MpPreference, netsh.exe) to disable the endpoint security solution (Microsoft Defender) and the firewall
- A misconfiguration in the SonicWall firewalls’ SSLVPN Default Users Group setting and the devices’ Virtual Office Portal
Exploiting improperly stored recovery codes
In a blog post published on Monday, Huntress threat analysts also pointed out a crucial error made by a security engineer at one of the targeted organizations: they stored Huntress recovery codes in plain text, in a file whose name made this very obvious.
“These recovery codes serve as a backup method for bypassing multi-factor authentication (MFA) and regaining account access. If compromised, they effectively allow an attacker to circumvent MFA entirely, impersonate the legitimate user, and gain full access to the Huntress console, significantly increasing the risk of further compromise or tampering with detection and response capabilities,” analysts Michael Elford and Chad Hudson explained.
And that is what the attackers used them for: they logged into the console with the security engineer’s account, and began closing active incident reports, removing previously isolated (ransomware infected) systems from isolation, and attempting to remove Huntress EDR agents from compromised endpoints.
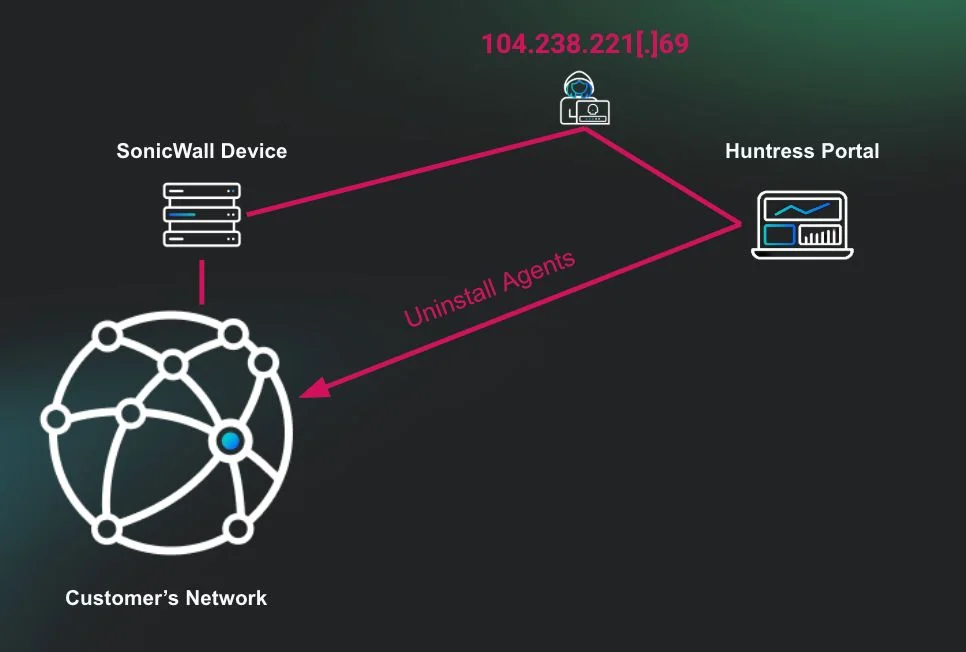
How the attackers uninstalled the EDR agents through the portal (Source: Huntress)
“Organizations should treat recovery codes with the same sensitivity as privileged account passwords,” the threat analysts noted.
Plaintext storage is a no-no – credentials and recovery codes should either be stored in a an encrypted password manager with a strong passphrase and without the autofill option switched on, or stored in an encrypted, password-protected file on an encrypted USB drive or hard disk.
In addition to this, they advise organizations to periodically regenerate recovery codes (if possible) and monitor login access for unusual logins.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!
