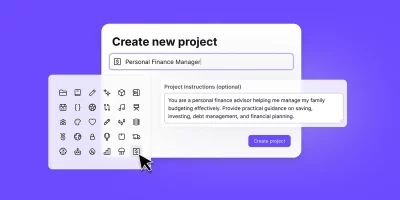
Proton expands Lumo AI assistant with encrypted, project-based workspaces
Lumo is Proton’s AI assistant, built with a focus on privacy and user control. It runs on Proton’s infrastructure and is designed so conversations are not used to train models …

Wine 11 brings major architectural work, synchronization changes, 600+ bug fixes
Wine, originally short for “Wine Is Not an Emulator,” is a compatibility layer that allows Windows applications to run natively on POSIX-compliant operating systems, including …

AuraInspector: Open-source tool to audit Salesforce Aura access control misconfigurations
Google and its Mandiant threat intelligence unit have released AuraInspector, an open-source tool aimed at auditing data access paths in Salesforce Experience Cloud …

Browser-in-the-Browser phishing is on the rise: Here’s how to spot it
Browser-in-the-Browser (BitB) phishing attacks are on the rise, with attackers reviving and refining the technique to bypass user skepticism and traditional security controls. …

Minimal Ubuntu Pro expands Canonical’s cloud security offerings
Canonical has released Minimal Ubuntu Pro images for use on public cloud platforms, aiming to give teams a smaller base image with a narrower software footprint. The solution …

Parrot OS shares its 2026 plans for security tools and platform support
Parrot OS is a Debian-based Linux distribution built for cybersecurity work. Security practitioners use it for penetration testing, digital forensics, malware analysis, and …

Enterprise security faces a three-front war: cybercrime, AI misuse, and supply chains
Security teams are dealing with pressures tied to AI use, geopolitical instability, and expanding cybercrime that reach beyond technical controls, according to findings from …

Rakuten Viber CISO/CTO on balancing encryption, abuse prevention, and platform resilience
In this Help Net Security interview, Liad Shnell, CISO and CTO at Rakuten Viber, discusses how messaging platforms have become critical infrastructure during crises and …

Turning cyber metrics into decisions leaders can act on
In this Help Net Security video, Bryan Sacks, Field CISO at Myriad360, explains how security leaders can measure cybersecurity in ways that matter to executives and boards. He …

Teaching cybersecurity by letting students break things
Cybersecurity students show higher engagement when the work feels tangible. A new study from Airbus Cybersecurity and Dauphine University describes what happens when courses …

What insurers expect from cyber risk in 2026
Technology shifts, policy decisions, and attacker behavior are changing at the same time, and their effects increasingly overlap. Insurers, brokers, and security teams are …

Cybersecurity jobs available right now: January 13, 2026
CISO CSIRO | Australia | Remote – No longer accepting applications As a CISO, you will lead and manage CSIRO’s cyber security strategy and program in alignment with the …