Phishing, software supply chain attacks greatest threats for businesses
Attackers continue to use phishing as a preferred attack method, but have been forced to adapt their approach as anti-phishing tools and techniques are becoming more sophisticated.
The phishing threat
“Phishing attacks have become increasingly polymorphic, which means attackers don’t use a single URL, domain, or IP address to send mail, but make use of a varied infrastructure with multiple points of attack. The nature of the attacks themselves has also evolved, with modern phishing campaigns ranging from short-span attacks that are active for just minutes to much longer high-volume campaigns,” Microsoft analysts have pointed out in the latest edition of the company’s Security Intelligence Report, which covers the period between January and December 2018.
The company has also noticed that phishers are increasingly using hosted infrastructure and other public cloud infrastructure to distribute malicious payloads, and compromised accounts to distribute malicious emails.
“Phishing promises to remain a problem for the foreseeable future because it involves human decisions and judgement in the face of persistent efforts by cybercriminals to make victims fall for their lures,” the analysts noted. And the lures are, unfortunately, many and diverse.
Attacks on software supply chains
“The first major software supply chain attack incident of 2018 occurred on March 6, when Windows Defender ATP blocked a massive campaign to deliver the Dofoil trojan,” the company noted.
The campaign was traced to a poisoned version of MediaGet, a BitTorrent client, whose update package was replaced with a malicious one that downloaded the code responsible for installing the Dofoil malware.
Throughout the year, other campaigns were spotted. In July, unknown attackers used the same trick to deliver a coin miner. The target were users a PDF editor application and the attackers succeeded by compromising the shared infrastructure in place between the vendor and one of its software vendor partners.
In other campaigns attackers compromised remote support solutions, hosting control panel solutions, browser extensions, WordPress plugins, Docker images, Python packages, scripts, Linux repositories, and npm modules.
“The threat of supply chain attacks is an industry-wide problem that requires attention from multiple stakeholders, including the software developers and vendors who write the code, the system administrators who manage software installations, and the information security community that finds these attacks and creates solutions to protect people and software from them,” the analysts pointed out.
Other threats
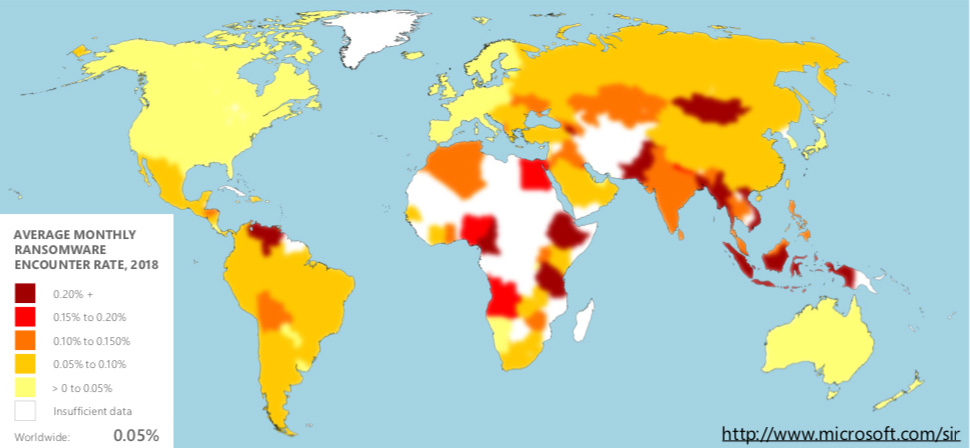
Many other threats are seemingly on a downward swing: the number of Microsoft machines that encountered ransomware in 2018 has declined by 73%, malware encounter rates decreased by 34%, cryptocurrency mining encounters by 36%, and drive-by download page encounters by 22%.
The analysts attribute the decline of ransomware to victims increasingly not paying the ransoms and companies being increasingly able to retrieve locked up files from their backups.
“Still, it continues to be a threat in some regions, primarily due to a lack of security hygiene, with occasional spikes in encounter rates,” they noted.
They also pointed out that while stealthy cryptomining might not immediately be a grave concern, the access achieved by the attackers could be a serious threat in the long run.
Advice for organizations
Microsoft urges organizations to implement the lowest cost techniques to steadily remove cheap and effective attack techniques.
These include avoiding using pirated software, mitigating credential theft risk, securing configurations, keeping machines updated and isolating those that can’t be, implementing email and browser protections (e.g., email gateways) and enabling host anti-malware and network defenses to get near real-time blocking responses from cloud.
Automatic creation of backups and keeping the safe is also important, as is teaching employees to spot phishing and social engineering attacks, to practice secure web browsing habits and to be on the lookout for signs of compromise (e.g., slowed down computers).
Finally, to protect against supply chain attacks, admins should apply the principle of least privilege across the organization, make it possible to download applications only from reliable sources, and restrict the applications that users can run.