North Korea’s IT workers are targeting firms beyond tech, crypto, and the U.S.
North Korea’s clandestine IT Worker (ITW) program, which is long known for targeting U.S. technology firms and crypto firms, has broadened its scope to attempt to infiltrate a variety of industries worldwide, including finance, healthcare, public administration, and professional services.
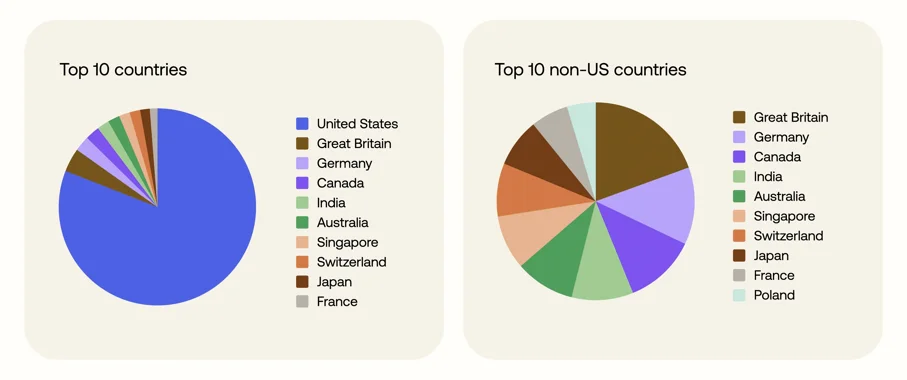
Okta’s threat researchers have identified over 130 identities associated with DPRK-linked facilitators and workers, which collectively pursued more than 6,500 interviews across 5,000+ companies until mid-2025, and have found that the threat is far more pervasive: 50% of targeted entities are not technology companies, and 27% of them lie outside of the United States. 
ITW operations have also expanded into other countries (Source: Okta)
What kind of placements are these workers aiming for?
According to Okta, organizations in every vertical offering remote or hybrid roles are now potential targets.

Beyond payroll diversion, successful placements allow these workers to access to sensitive systems and networks, opening the door to data exfiltration, extortion, or intelligence gathering. 
DPRK IT Workers aren’t just applying for coding roles anymore: they are increasingly targeting finance, payments processing, and engineering support positions.
While they continue to focus overwhelmingly on remote software development and IT consulting roles, in tech companies, service providers, and IT consultancies, Okta has also noticed a marked increase in DPRK-linked job interviews within:
- AI-focused organizations
- Healthcare organizations and medical technology providers (mobile application development, customer service systems, and electronic record-keeping platforms)
- Banks, insurance firms, FinTech companies (software development, but also back-office and financial processing roles in areas like payroll and accounting)
- Outsourcing and IT service providers, and even
- Government and public administration organizations in the US, Middle East, and Australia
“Although our data does not confirm whether any of these interviews resulted in employment, the attempts demonstrate that government agencies are not immune to the campaign,” Okta noted.
“More significant is the exposure to public administration via government contractors, service providers and consultancies. These organizations often have extensive access to government networks and sensitive projects, but face high hiring volumes, fast turnaround times, and large pools of remote workers.”
Recommendations for organizations
DPRK ITW units have learned from earlier missteps and have refined their methods to bypass traditional identity and vetting controls.
To counter this threat, Okta advises organizations to adopt a multi-layered defense that will include:
- Rigorous identity verification: Use government-issued ID, cross-check geolocation and payroll details, and leverage third-party verification services
- Advanced screening processes: Train recruiters to detect red flags (e.g. inconsistent time zones, refusal of live interviews) and use structured technical tasks under supervision.
- Least-privilege access and segregation: Start new or contingent workers with minimal permissions and segment network access.
- Vendor / third-party safeguards: Enforce equivalent identity controls, device security, and audit rights in contracts.
- Insider-threat programs and awareness: Equip HR, IT, and security teams to identify suspicious behavior and provide safe reporting channels.
- Collaboration and intelligence sharing: Work with law enforcement, ISACs, and peer organizations to share indicators and suspicious candidate patterns.
- Simulated hiring red-team and risk exercises: Test recruitment pipelines as if under DPRK infiltration to uncover gaps proactively, and update incident response plans.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!