When IT fails, OT pays the price
State groups, criminal crews, and hybrid operators are all using familiar IT entry points to reach systems that support industrial processes, according to the latest Operational Technology Threat Report from Trellix.
The report covers attacks observed from April through September 2025 and describes a pattern of coordinated activity that blends espionage, criminal extortion, and cyber operations linked to geopolitical conflict.
A concentrated target landscape
Manufacturing accounted for 41.5% of detections, and transportation and shipping accounted for 27.6%. Utilities, energy, and aerospace and defense made up most of the remaining activity. This pattern is expected because these sectors depend on integrated industrial systems and face high impact when operations are disrupted.
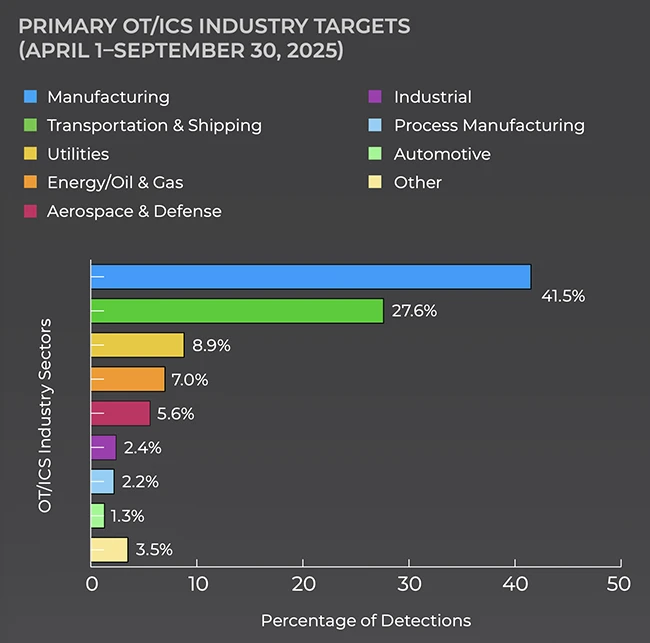
Most detections occurred on IT infrastructure inside OT focused organizations. Mail systems, perimeter gateways, and endpoints served as the entry points. Attackers avoided direct attempts on hardened controllers and instead went after exposed business systems that connect to Level 3 and Level 4 environments.
State backed operations remain the dominant source of OT risk
The Sandworm group accounted for almost one third of observed OT related intrusions over the past several years. Activity during the reporting period centered on Ukrainian energy and telecommunications networks. Sandworm used Industroyer2 to manipulate substation operations and deployed wipers to slow recovery. Their operations show an intent to combine destructive tools with timing that aligns with physical conflict.
TEMP.Veles, also known as XENOTIME, remains the most advanced threat to safety instrumented systems. The group’s history with TRITON stands out because it involved attempts to alter safety logic. Recent activity suggests continued reconnaissance in energy and chemical organizations. The targeting of engineering workstations and safety networks points to an effort to maintain access until a future moment of strategic value.
Iranian groups APT33 and APT34 continued operations focused on aviation, petrochemical, and government networks. Both expanded from espionage to destructive activity. Their campaigns rely on credential theft, abuse of web facing infrastructure, and wiper deployment. The shift shows a move toward coercion that mixes theft with disruption.
Ransomware groups are learning the OT playbook
Criminal groups are now demonstrating a better understanding of industrial dependencies. The Qilin group carried out 63 confirmed attacks against industrial entities since mid 2024 and has focused on energy distribution and water utilities. Their use of Windows and Linux payloads gives them wider reach inside mixed environments. Several incidents involved encryption of shared engineering resources and historian systems, which caused operational delays even when controllers remained untouched.
These trends show that financial motives and OT aware methods are converging. Ransomware operators know that operational disruption increases leverage, so they are adapting their payloads to reach systems positioned between IT and OT.
Techniques that cross the IT and OT boundary
Across intrusions, attackers favored techniques that exploit weak segmentation. PowerShell activity made up the largest share of detections, followed by Cobalt Strike. The findings show that adversaries rarely need ICS specific exploits at the start of an attack. They rely on stolen accounts, remote access tools, and administrative shares to move toward engineering assets.
Once inside the right network segment, they shift to industrial protocols. Modbus, DNP3, and IEC 61850 allow malicious commands to blend with legitimate traffic. This creates visibility challenges for defenders without continuous inspection of process level communications. Skilled operators then deploy specialized tools such as Industroyer for power distribution or TRITON for safety controllers.
Vulnerability trends reflect the same pressure points
The vulnerability data reinforces the emphasis on the boundary between enterprise systems and industrial systems. Ongoing exploitation of Cisco ASA and FTD devices, including attacks that modified device firmware. Several critical flaws in SAP NetWeaver and other manufacturing operations software were also exploited, which created direct pivot points into factory workflows.
Recent disclosures affecting Rockwell ControlLogix and GuardLogix platforms allow remote code execution or force the controller into a failed state. Attacks on these devices pose immediate availability and safety risks.
On average it takes more than 180 days to deploy patches inside OT networks because updates require scheduled downtime. As a result, vulnerable services often remain unpatched long after fixes are released.
“Regular training sessions that coach employees about emerging threats, phishing attempts, and safe handling of sensitive information can significantly reduce risks. Furthermore, involving employees in security best practices and readiness testing fosters a culture of resilience to the entire organization,” said John Fokker, VP, Threat Intelligence Strategy at Trellix.