Who’s on the other end? Rented accounts are stress-testing trust in gig platforms
Fraud has become a routine part of gig work for many earners, and the ways workers respond are creating new security problems for platforms. A recent TransUnion study of U.S. gig workers shows broad exposure to fraud, inconsistent reporting, and growing participation in prohibited practices such as account renting and selling.
Fraud is a common part of gig work
34% of those surveyed said they had been defrauded by a consumer while working on a gig platform. Fraud included payment disputes, chargebacks, and other forms of consumer abuse that led to lost income. Tip baiting also appeared frequently. Many described customers offering large tips to secure faster service and then reducing the tip after the job was completed.
Those who experienced fraud or abuse reported stronger expectations for intervention by service operators. They wanted companies to verify user identities, validate delivery addresses, and remove users with repeated bad behavior. These expectations extended beyond physical safety to identity protections during onboarding and during active work.
Safety tools and trust do not move together
The study showed a disconnect between victimization and confidence in safeguards offered by gig providers. Individuals who had been defrauded expected stronger protections, while also expressing less confidence that in app safety features would help during an incident. Location tracking and emergency buttons did not consistently lead to a sense of security for people who had already experienced harm.
This gap matters for cybersecurity and trust teams because it shows the difference between deployed controls and perceived protection. Safeguards exist across services, though confidence depends on identity checks, enforcement, and follow through after reports.
Incidents often go unreported
Despite frequent exposure to fraud and abuse, reporting remained uneven. Participants said they reported incidents to the company running the service, while fewer contacted law enforcement. Others adjusted their behavior instead, including switching marketplaces or limiting the types of jobs they accepted.
Some respondents said they considered leaving gig work after a serious incident but continued because they needed the income. This dynamic can discourage reporting, especially when people expect delays, lost earnings, or account restrictions during investigations. When incidents go unreported or lack detail, trust and safety teams receive incomplete signals about where controls are breaking down.
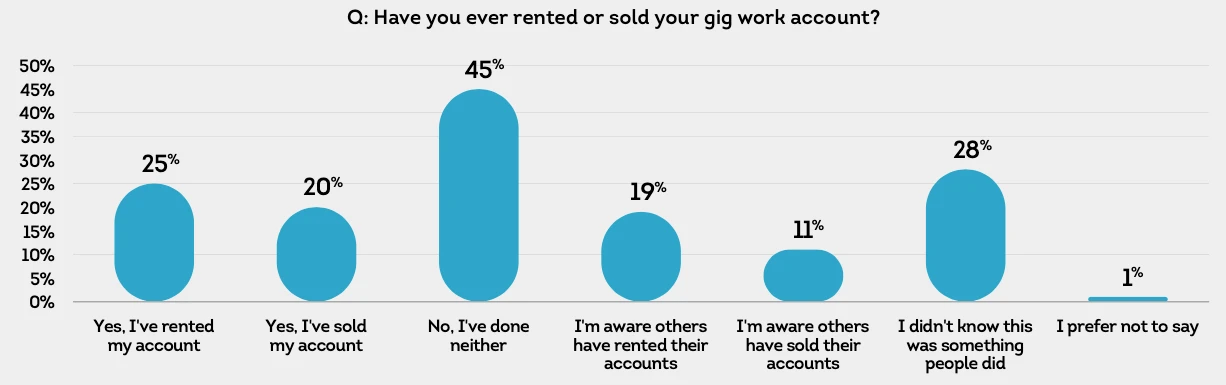
Account sharing moves into the open
One of the most consequential findings involved account renting and selling. Nearly half of those surveyed said they had rented or sold a gig account or were aware of others doing so. About one quarter said they had personally rented their account.
Younger earners reported this behavior more often than older groups. Account sharing allows unverified individuals to perform work under another person’s identity, bypassing background checks and device history. This introduces risk for consumers, account holders, and platforms at the same time.
From a cybersecurity perspective, account sharing weakens core identity assumptions. Activity attribution becomes unreliable. Device trust declines. Enforcement grows more difficult when the registered account holder and the active user are different people.
“Renting and selling worker accounts places consumers, workers and platforms at risk,” said Colleen Thiry, director of TransUnion’s gig economy business. “Allowing someone who has not been vetted and verified to provide services leaves consumers prone to fraud and physical danger, and it exposes the account owner and the platform to liability for any harm that occurs.”
Fake users remain part of the ecosystem
Survey participants also reported regular interaction with fake users and fake listings. Fewer than half believed platforms were successful at blocking unauthorized users. Even so, the presence of fake activity did not strongly affect decisions to join or remain on a service.
This suggests a level of tolerance. Some may accept fraud exposure as long as income remains available. That tolerance shifts responsibility to providers, which must manage fraud risk without relying on churn to drive change.
Identity verification stands out as a priority
Across the study, identity verification emerged as the most consistent expectation. Those who experienced fraud wanted stronger checks during onboarding and ongoing confirmation that the person using an account matched the registered identity.
These expectations applied to both sides of the marketplace. Respondents supported verification of users, delivery addresses, and devices. The findings point toward layered identity approaches that combine identity data, device intelligence, and behavioral signals.