The internet’s oldest trust mechanism is still one of its weakest links
Attackers continue to rely on domain names as an entry point into enterprise systems. A CSC domain security study finds that large organizations leave this part of their attack surface underprotected, even as attacks become more frequent. The research examined the Forbes Global 2000 and compared them with the world’s top 100 privately held unicorn companies.
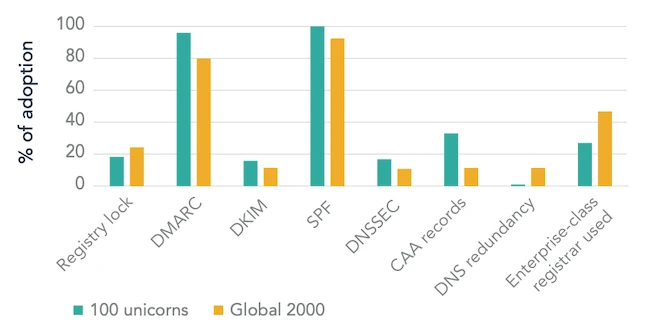
Domain security adoption: 100 unicorns vs Global 2000 (Source: CSC)
Domains sit outside standard security controls
Domains operate outside the firewall but support email, authentication, websites, APIs, and partner access. Attackers exploit this gap by hijacking domains, registering lookalikes, or reusing lapsed names.
Phishing, business email compromise, malware delivery, and impersonation attacks often depend on domains that appear legitimate. Dormant and forgotten domains worsen the problem because they escape monitoring while remaining usable.
DNS availability becomes a weak point
Large companies continue to add baseline protections, though adoption remains uneven. Email authentication shows the most consistent improvement, driven by phishing activity and regulatory pressure. Organizations still leave email domains partially protected, which allows spoofing to persist.
Other protections see much slower uptake. Controls designed to prevent unauthorized domain changes or protect DNS integrity remain uncommon across the Global 2000. These gaps increase exposure to hijacking and traffic redirection, especially when attackers compromise registrar accounts.
DNS redundancy stands out as a concern. Adoption declined year over year, with many organizations relying on a single cloud provider for DNS services.
Cost pressures and cloud consolidation appear to drive this trend. Single provider DNS setups increase exposure to outages and targeted attacks. Dual infrastructure remains uncommon, even though DNS availability supports email, authentication, and application access.
Registrar choice affects security posture
Registrar selection affects domain security. Organizations using enterprise focused registrars show higher adoption of advanced protections, including locks that prevent unauthorized domain changes.
Consumer oriented registrars tend to emphasize simplicity and cost. Organizations that rely on them often lack access to protections that limit the impact of account compromise or social engineering. Risk increases as domain portfolios grow and change.
Industry gaps remain visible
Technology driven sectors perform better overall. IT software and services lead domain security rankings, followed by media, retail, and telecommunications. Banking and semiconductor firms showed notable improvement over the past year.
Construction, utilities, and mining remain among the lowest performing sectors. Many fall under critical infrastructure classifications, which raises concern given growing regulatory requirements tied to cyber risk management.
Regional trends show Asia Pacific organizations improving faster than other regions, though overall adoption still trails Europe and the Americas by a wide margin.
Third party domains drive brand abuse
Brand impersonation through domain spoofing remains widespread. Lookalike domains tied to major brands are often owned by third parties. Some appear inactive while still supporting email activity.
Inactive domains with mail records allow attackers to send phishing messages that appear associated with trusted brands. Others are parked with advertising networks or held for later use. A smaller portion hosts malicious content, though dormant domains can be activated quickly.
Financial services brands attract a large share of this activity, reflecting their value as targets. Technology and service firms also remain frequent targets due to broad user bases and established trust.
Unicorn companies show mixed maturity
Unicorns score higher than the Global 2000 in five of eight domain security categories. Strengths center on DNS record based controls such as SPF, DKIM, DMARC, DNSSEC, and CAA records.
These measures are low cost and often managed by small technical teams with DNS expertise, allowing younger companies to deploy baseline protections early.
Gaps appear in infrastructure related areas. DNS redundancy and registry lock adoption lag, and many unicorns rely on consumer grade registrars. These limitations become more pronounced as operations scale.
Most unicorns fall into a middle security range. They invest in email protection while leaving other areas less developed.
“Domain names, DNS, and brand trust are fundamental to our online presence. Long-overlooked dependencies will compound cyber risks as new AI and IT stacks emerge,” said Vincent D’Angelo, senior director at CSC. “It’s encouraging to see unicorns adopting strong domain security practices early, yet much work remains. As these new tech platforms scale, continued prioritization of domain security will be essential to reducing cybercrime, strengthening trust and safety, and lowering systemic risk across customer and partner supply chains.”
Across the Global 2000, most companies have implemented fewer than half of the recommended domain security measures. A small number still show no meaningful protections in place.
Perfect scores remain rare, reflecting the difficulty of managing domain security consistently across large, global organizations.