Help Net Security

Fixing silent failures in security controls with adversarial exposure validation
Organizations often operate as if their security controls are fully effective simply because they’re deployed, configured, and monitored. Firewalls are in place, …

Download: Cyber defense guide for the financial sector
Data breaches cost more for financial organizations than they do for those in many other industries. In attempting to strengthen your financial organization’s …

Are we headed for an AI culture war?
In this Help Net Security video, Matt Fangman, Field CTO at SailPoint, discusses whether an AI culture war is inevitable. He explores the rise of AI agents as a new identity …

Cyber defense cannot be democratized
The democratization of AI has fundamentally lowered the barrier for threat actors, creating a bigger pool of people who can carry out sophisticated attacks. The so-called …

Week in review: Several companies affected by the Salesloft Drift breach, Sitecore 0-day vulnerability
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Zscaler, Palo Alto Networks, SpyCloud among the affected by Salesloft Drift …

September 2025 Patch Tuesday forecast: The CVE matrix
September 2025 Patch Tuesday is now live: Microsoft, Adobe, SAP deliver critical fixes for September 2025 Patch Tuesday We work in an industry driven by Common Vulnerabilities …

Smart ways CISOs can do more with less
In this Help Net Security video, Jill Knesek, CISO at BlackLine, shares practical strategies for CISOs navigating tighter budgets. From maximizing existing tools and vendor …
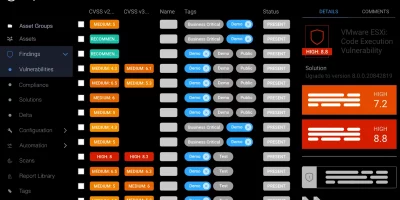
CyberFlex: Flexible Pen testing as a Service with EASM
About CyberFlex CyberFlex is an Outpost24 solution that combines the strengths of its Pen-testing-as-a-Service (PTaaS) and External Attack Surface Management (EASM) solutions. …

BruteForceAI: Free AI-powered login brute force tool
BruteForceAI is a penetration testing tool that uses LLMs to improve the way brute-force attacks are carried out. Instead of relying on manual setup, the tool can analyze HTML …

Detecting danger: EASM in the modern security stack
In today’s complex threat environment, the challenge for security professionals isn’t just defeating threats, it’s finding your vulnerabilities in the first place. That’s …

Five habits of highly secure development teams
In this Help Net Security video, Brendon Collins, Principal Consultant at Optiv, explores how organizations can embed security and privacy into the software development …

What the GitGuardian secrets sprawl report reveals about leaked credentials
In this Help Net Security video, Dwayne McDaniel, Senior Developer Advocate at GitGuardian, presents findings from The State of Secrets Sprawl 2025. McDaniel explains why …