cybersecurity

GenAI is fueling smarter fraud, but broken teamwork is the real problem
More than 80 percent of large U.S. companies were targeted by socially engineered fraud in the past year, according to Trustmi’s 2025 Socially Engineered Fraud & Risk …

New framework aims to outsmart malware evasion tricks
Attackers have learned how to trick machine learning malware detectors with small but clever code changes, and researchers say they may finally have an answer. In a new paper, …

Finding connection and resilience as a CISO
With sensitive information to protect and reputational risk always in the background, it isn’t easy for security leaders to have open conversations about what’s working and …

AI isn’t taking over the world, but here’s what you should worry about
In this Help Net Security video, Josh Meier, Senior Generative AI Author at Pluralsight, debunks the myth that AI could “escape” servers or act on its own. He explains how …

Maritime cybersecurity is the iceberg no one sees coming
Maritime transport, the backbone of global trade, is adapting to shifting economic, political, and technological conditions. Advances in technology have improved efficiency, …

Can AI make threat intelligence easier? One platform thinks so
When analysts at RH-ISAC found themselves spending 10 hours a week just collecting threat intelligence, they knew their process wasn’t sustainable. They were manually tracking …

How CISOs are balancing risk, pressure and board expectations
AI has moved to the top of the CISO agenda. Three in five CISOs see generative AI as a security risk, with many worried about sensitive data leaking through public tools. At …

AI is becoming a core tool in cybercrime, Anthropic warns
A new report from Anthropic shows how criminals are using AI to actively run parts of their operations. The findings suggest that AI is now embedded across the full attack …

AI Security Map: Linking AI vulnerabilities to real-world impact
A single prompt injection in a customer-facing chatbot can leak sensitive data, damage trust, and draw regulatory scrutiny in hours. The technical breach is only the first …

How compliance teams can turn AI risk into opportunity
AI is moving faster than regulation, and that creates opportunities and risks for compliance teams. While governments work on new rules, businesses cannot sit back and wait. …

Hottest cybersecurity open-source tools of the month: August 2025
This month’s roundup features exceptional open-source cybersecurity tools that are gaining attention for strengthening security across various environments. Buttercup: …
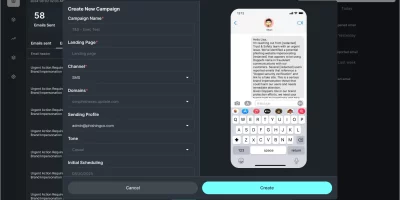
What CISOs can learn from Doppel’s new AI-driven social engineering simulation
Doppel has introduced a new product called Doppel Simulation, which expands its platform for defending against social engineering. The tool uses autonomous AI agents to create …