Number of corporate credentials exposed on the dark web increased by 429%
While there has been a year-over-year decrease in publicly disclosed data breaches, an Arctic Wolf report reveals that the number of corporate credentials with plaintext passwords on the dark web has increased by 429 percent since March.
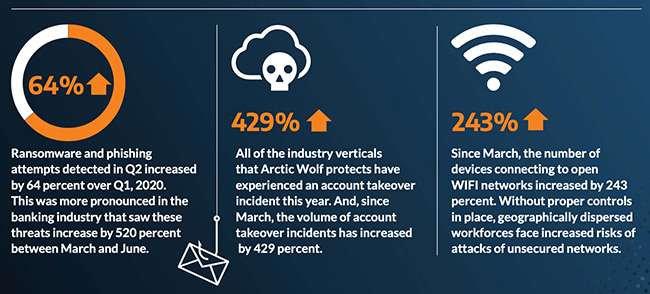
For a typical organization, this means there are now, on average, 17 sets of corporate credentials available on the dark web that could be used by hackers.
With access to just one corporate account, attackers can easily execute account takeover attacks, which allow them to move laterally within an organization’s corporate network and gain access to sensitive data, intellectual property, competitive information, or funds.
Cybersecurity incidents now occur after hours
The sharp increase in corporate credential leaks underscores the need for organizations to have dedicated 24×7 monitoring of their network, endpoint, and cloud environments in order to prevent targeted attacks that could happen at any time.
Of the high-risk security incidents observed, 35% occur between the hours of 8:00 PM and 8:00 AM, and 14% occur on weekends; times when many in-house security teams are not online.
“The cybersecurity industry has an effectiveness problem. Every year new technologies, vendors, and solutions emerge. Yet, despite this constant innovation, we continue to see breaches in the headlines.
“The only way to eliminate cybersecurity challenges like ransomware, account takeover attacks, and cloud misconfigurations is by embracing security operations capabilities that fully integrate people, processes, and technology,” said Mark Manglicmot, VP Security Services, Arctic Wolf.
COVID-19 increasing the number of security operations challenges
- A 64 percent increase in phishing and ransomware attempts – Hackers have created new phishing lures around COVID-19 topics and adapted traditional lures seeking to take advantage of remote workers.
- Critical vulnerability patch time has increased by 40 days – A combination of higher common vulnerabilities and exposures (CVE) volumes, more critical CVEs, and the emergence of a remote workforce have significantly slowed the patching programs at many organizations.
- Unsecured Wi-Fi usage is up by over 240 percent – Remote workforces connecting to open and unsecured Wi-Fi networks outside of their office or home are now facing increased risks of malware exposure, credential theft, and browser session hijacking.