Hackers breached U.S. government agencies via compromised SolarWinds Orion software
A “highly sophisticated” hacking group has breached the U.S. Treasury Department, the U.S. Department of Commerce’s National Telecommunications and Information Administration (NTIA), other government agencies and private sector companies (including, apparently, FireEye) via compromised SolarWinds Orion software.
A supply chain attack
According to reports by FireEye and Microsoft, the hacking group managed to insert a backdoor (signed with SolarWinds’ legitimate certificates) into a DLL file used by the SolarWinds Orion platform, which organizations use for IT monitoring and management.
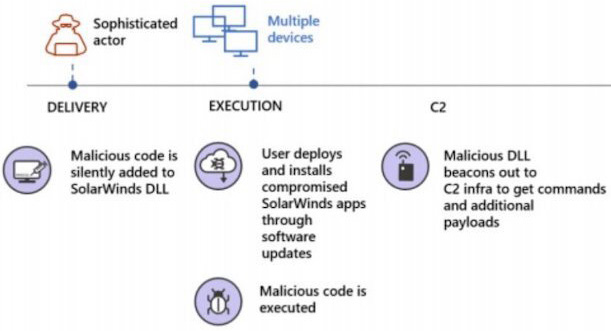
“Although we do not know how the backdoor code made it into the library, from the recent campaigns, research indicates that the attackers might have compromised internal build or distribution systems of SolarWinds,” Microsoft noted, and added that the backdoor was distributed via automatic update platforms or systems in target networks.
Once inside, the attackers moved laterally and proceeded to steal data.
According to Microsoft, they used administrative permissions acquired through an on-premises compromise to gain access to an organization’s trusted SAML token-signing certificate and they forged SAML tokens that impersonate any of the organization’s existing users and accounts (which allowed them to access to on-premises and cloud resources). They also made changes to the organizations’ Azure Active Directory settings to facilitate long term access.
SolarWinds has confirmed that SolarWinds Orion Platform software builds for versions 2019.4 HF 5 through 2020.2.1, released between March 2020 and June 2020, have been compromised and that a “clean” version (2020.2.1 HF 1) is now available for download.
“An additional hotfix release, 2020.2.1 HF 2 is anticipated to be made available Tuesday, December 15, 2020. We recommend that all customers update to release 2020.2.1 HF 2 once it is available, as the 2020.2.1 HF 2 release both replaces the compromised component and provides several additional security enhancements,” the company noted.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an Emergency Directive instructing “all federal civilian agencies to review their networks for indicators of compromise and disconnect or power down SolarWinds Orion products immediately.”
Who’s behind these attacks?
SolarWinds’ customers include US telecoms, all five branches of the US Military, various US federal agencies (including the Pentagon, State Department, and the Office of the President of the United States), more than 425 of the US Fortune 500 companies, and many higher education institutions.
FireEye says that this campaign may have begun as early as Spring 2020 and the attackers gained access to government, consulting, technology, telecom and extractive entities in North America, Europe, Asia and the Middle East.
Washington Post sources say that the hacker group behind these attacks is APT29 (aka Cozy Bear), which has ties with the Russian Foreign Intelligence Service. Kremlin spokesman Dmitry Peskov said that Russia had nothing to do with the attacks on the U.S. Treasury and Commerce departments.
UPDATE (December 14, 2020, 8:40 a.m. PT):
SolarWinds has filed a report with the U.S. SEC, in which it stated that “the vulnerability … was introduced as a result of a compromise of the Orion software build system and was not present in the source code repository of the Orion products.”
Also, that it “currently believes the actual number of customers that may have had an installation of the Orion products that contained this vulnerability to be fewer than 18,000,” and that the attackers likely breached the company by compromising company emails (they use Microsoft Office 365 for its email and office productivity tools).