Remote work hazards: Attackers exploit weak WiFi, endpoints, and the cloud
Infoblox unveils a global report examining the state of security concerns, costs, and remedies. As the pandemic and uneven shutdowns stretch into a third year, organizations are accelerating digital transformation projects to support remote work. Meanwhile, attackers have seized on vulnerabilities in these environments, creating more work and larger budgets for security teams.
1,100 respondents in IT and cybersecurity roles in 11 countries – United States, Mexico, Brazil, United Kingdom, Germany, France, the Netherlands, Spain, United Arab Emirates, Australia, and Singapore – participated in the survey.
The state of remote work security
The surge in remote work has changed the corporate landscape significantly – and permanently. 52% of respondents accelerated digital transformation projects, 42% increased customer portal support for remote engagement, 30% moved apps to third party cloud providers, and 26% shuttered physical offices for good. These changes led to the additions of VPNs and firewalls, a mix of corporate and employee owned devices as well as cloud and on-premises DDI servers to manage data traffic across the expanded network.
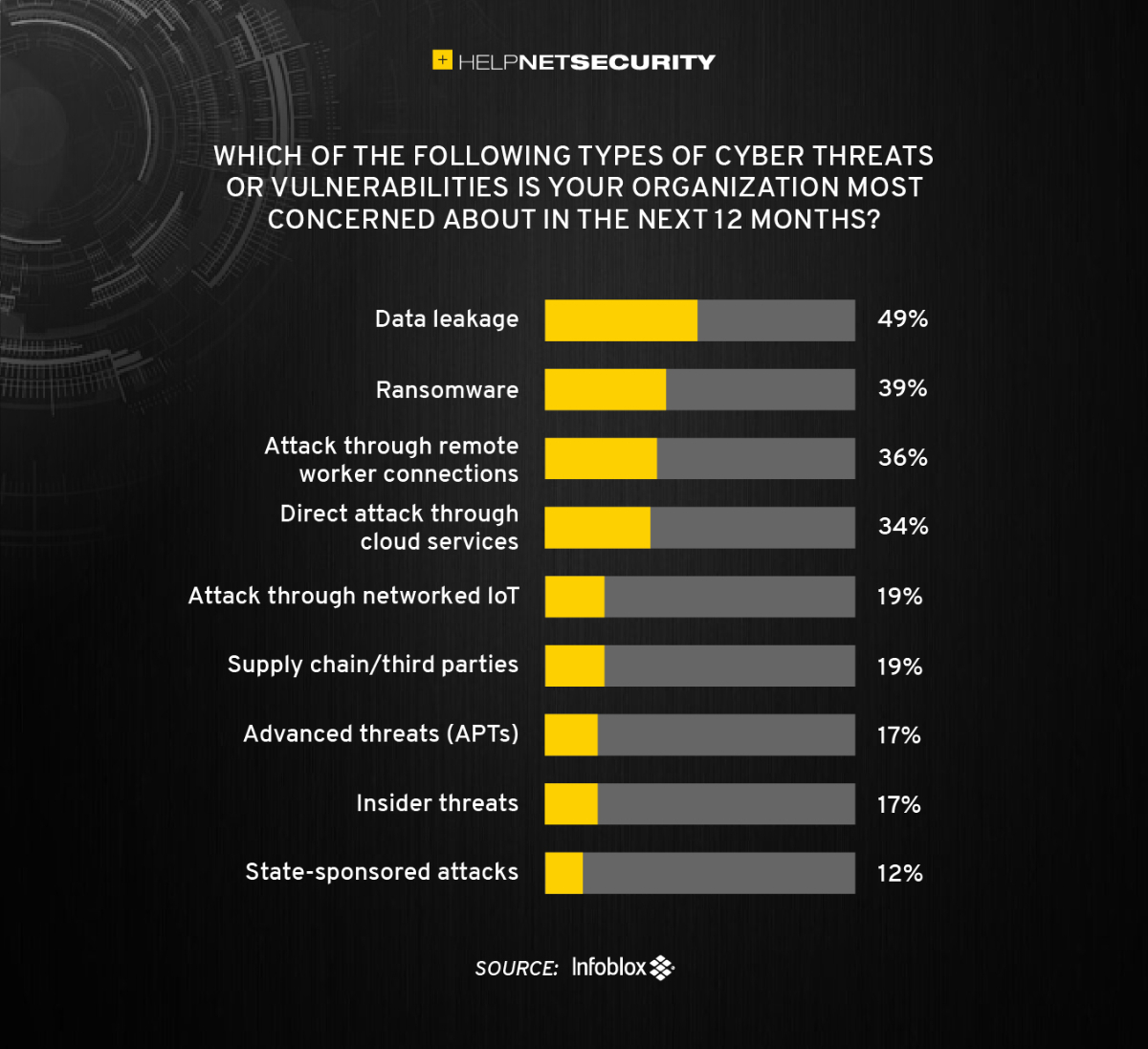
The hybrid workforce reality is causing greater concerns with data leakage, ransomware and attacks through remote access tools and cloud services. Respondents indicate concerns about their abilities to counter increasingly sophisticated cyberattacks with limited control over employees, work-from-home technologies, and vulnerable supply chain partners. The sophistication of state-sponsored malware also is a source of worry for many.
Organizations have good reason to worry: 53% of respondents experienced up to five security incidents that led to at least one breach. Though ransomware often grab headlines, phishing is the most common conduit for illegal entry. Attacks tended to originate on WiFi access points, employee-owned endpoints, or the cloud. Overall, 43% suffered at least $1 million in direct and indirect losses.
Organizations are buying cloud-first security tools to protect their hybrid environments. 59% of respondents saw bigger budgets in 2021 and nearly 75% anticipate an increase in 2022. They are creating a defense-in-depth strategy using everything from endpoint and network security to cloud access security brokers, DNS security, and threat intelligence services to defend their expanded attack surface. Network data is taking center stage for threat hunting. 40% mostly relied on network flow data, 39% on systems-specific vulnerability information, 39% DNS queries, and 37% outside threat intelligence services.
Interest in secure access service edge (SASE) frameworks is accelerating. As assets, access and security move out of the network core to the edge with the push for virtualization, 53% have already partially or fully implemented SASE and another 28% intend to do so.
“The pandemic shutdowns over the past two years have reshaped how companies around the world operate,” said Anthony James, VP of Product Marketing at Infoblox. “Cloud-first networks and corresponding security controls went from nice-to-have features to business mainstays as organizations sent office workers to work from home. To address the spike in cyberattacks, security teams are turning to DNS security and zero trust models like SASE for a more proactive approach to protecting corporate data and remote devices.”