The identity mess your customers feel before you do
Customer identity has become one of the most brittle parts of the enterprise security stack. Teams know authentication matters, but organizations keep using methods that frustrate users and increase risk. New research from Descope shows how companies manage customer identity and the issues that have been building in the background.
A growing gap between belief and practice
The findings show a mismatch between what security leaders say they value and what they deploy. Organizations agree that authentication is important to their business. A large share also believes that stronger methods improve customer experience. Despite this, 87% of organizations still depend on passwords or other high friction approaches. Only a small fraction believes these methods work well for user experience or security.
Companies continue to deal with fraud, repeated account recovery cycles, and engineering costs tied to outdated systems. While teams understand the problem, limited resources, competing priorities, and pressure to keep shipping new features push identity work aside.
Passwords dominate, even while everyone dislikes them
Organizations know passwords hurt security and customer experience. Even so, most remain tied to them because migrations feel costly or disruptive. Only a very small percentage of respondents believe passwords are the most effective option, but over two thirds still use them as a primary method.
Most organizations claim to use MFA somewhere in their environment, but few apply it across all customer facing applications. This uneven coverage exposes companies to predictable fraud and leaves gaps that attackers exploit. MFA adoption often stalls because internal teams lack time, budget, or expertise to advance the work.
Over 70% of organizations plan to adopt passkeys or have already taken initial steps.
Teams do not feel confident that their current systems can support passkeys without significant refactoring. Others struggle with internal alignment because product, engineering, marketing, and security teams do not always agree on how to prioritize customer identity upgrades. This leads to a hybrid model where passkeys are supported in a few places while passwords remain the default.
Developers carry the weight
Over half of organizations rely on developers who are not specialists in authentication. These teams juggle identity work alongside core product duties, which leads to slow progress, inconsistent implementation, and recurring defects.
Decision makers admit that they underestimate the time developers spend on authentication. In many organizations, identity work drops down the backlog until a breach, an outage, or lost revenue forces renewed attention. Context switching is common. Developers move between authentication, compliance requirements, and product enhancements, which increases the likelihood of mistakes and slows delivery.
“Engineering and identity teams are trying to fit square pegs into round holes when it comes to customer identity. Maintaining homegrown or workforce-based solutions with overstretched development teams is a recipe for falling behind as user needs evolve, new product needs arise, or AI agents are added to the mix,” said Rishi Bhargava, co-founder of Descope.
Security and customer experience pull in different directions
Authentication issues undermine revenue as well as security. Organizations report that user dropoff during login, delays in engineering delivery, and abandoned transactions stem from outdated authentication flows. These issues rarely show up as a single budget line, but they accumulate into lost revenue and higher operating costs.
Companies with more than 20,000 employees report higher rates of breaches and customer support strain tied to authentication. Scale magnifies the burden because fragmented systems and inconsistent policies create more work for security and engineering teams.
Nearly three quarters of respondents say finding the right balance between security and customer experience is difficult. Teams have different priorities. Security teams focus on risk reduction. Product teams focus on conversion and retention. Identity teams, where they exist, try to link both.
The result is often a patchwork of approaches that satisfies no one. Some organizations introduce controls that slow down legitimate users. Others reduce friction in ways that create openings for attackers. Because these decisions involve multiple stakeholders, progress is slow and often inconsistent across applications.
AI driven automation is about to strain customer identity systems
Agentic AI is set to make customer identity more complicated. Automated activity will increase on every front, from routine actions taken on behalf of legitimate users to large scale attacks that target login and account creation flows.
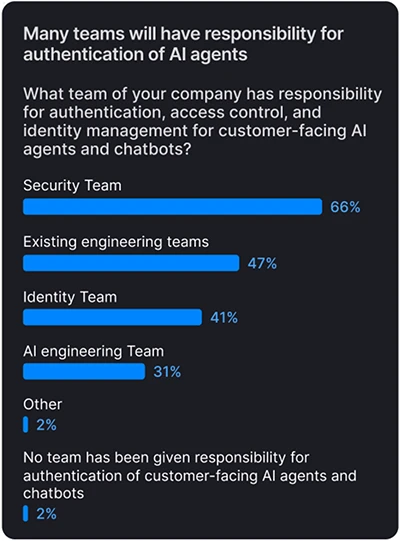
Security teams will face more traffic to evaluate and less certainty about what reflects user intent. Attackers will use AI to run high volumes of account takeover attempts and to create synthetic identities that blend in with normal behavior.
A range of authentication setups is not ready for this environment because they rely on passwords or other static checks that cannot adapt to rapid shifts in activity. Organizations will need identity systems that can adjust to changing patterns, flag suspicious behavior early, and still give trustworthy users a smooth experience.