When the Olympics connect everything, attackers pay attention
Global sporting events bring a surge of network traffic, new systems, and short term partnerships. That mix draws attention from cyber threat actors who see opportunity in scale and distraction. A new Palo Alto Networks threat study on the Milan Cortina 2026 Winter Olympic Games outlines how attackers are expected to operate across the event’s digital ecosystem, from ticketing platforms to telecom infrastructure.
A target-rich environment
Large events depend on fast deployment. Temporary venues, pop up networks, contractors, and local suppliers all connect systems under tight timelines. The study describes this environment as one where attackers benefit from complexity and trust between organizations.
Past Olympics provide reference points. The report notes disruptions to WiFi and digital services during PyeongChang 2018, attempted sabotage activity before Tokyo 2024, and a spike in DDoS activity and phishing during Paris 2024. Milan Cortina is expected to attract more than three billion viewers worldwide, raising the stakes for disruption and fraud.
Attackers cluster around three incentives. Financial gain includes ransomware, fraud, and scams aimed at fans and vendors. Intelligence collection focuses on diplomats, officials, and executives attending the Games. Public disruption attracts hacktivist groups seeking attention for political causes.
Ransomware groups move fast
Financially motivated groups remain a central concern. The study describes ransomware actors targeting ticketing systems, event websites, and supporting infrastructure. Disruption creates pressure, while data theft raises reputational and legal risk.
One example cited in the report involves a ransomware group that has compromised more than 500 victims since 2022. The group relies on email bombing and social engineering to trick users into granting remote access. Researchers observed cases where initial access and data exfiltration happened within 14 hours.
Scams aimed at attendees also feature prominently. Fake ticket sites, malicious QR codes, and fraudulent mobile apps are expected to circulate before and during the Games. These campaigns tend to scale quickly due to the volume of visitors and the urgency around travel and schedules.
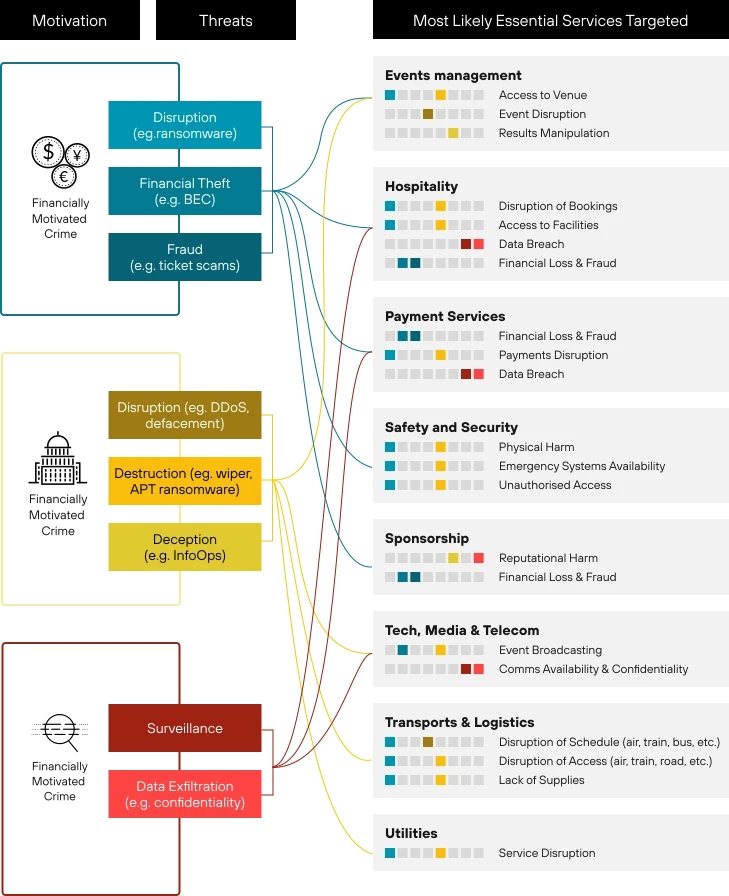
Critical services and associated threat-actor motivations (Source: Palo Alto Networks)
Espionage groups follow the people
Nation state actors approach the event with a focus on long term access and intelligence collection. The Games bring together political leaders, government staff, and executives who rely on shared infrastructure for connectivity.
The report highlights phishing as a common entry point. Spoofed websites and emails with weaponized attachments remain common. Once inside, attackers use custom tooling for command and control, tunneling, and persistence.
Chinese and Russian linked groups are cited as examples based on prior activity against government and telecom targets. Researchers note that these actors often operate inside ecosystems for months or years, collecting data while avoiding detection.
Hacktivists aim for visibility
Hacktivist groups pursue disruption and exposure. The study outlines a typical pattern that starts with scanning for exposed systems, followed by website defacement, data leaks, or DDoS attacks. Social media accounts and live streams also attract attention due to their public reach.
These campaigns often combine technical attacks with information operations. Stolen documents or personal data may be released to shape narratives and apply pressure. The global audience of the Winter Games amplifies the impact of these actions.
Social engineering stands out
Across all threat categories, social engineering appears as a consistent success factor. The report states that in 76% of phishing cases reviewed, attackers gained access through business email compromise. Messages impersonated executives, vendors, or partners to push fraudulent payments or system changes.
Advances in AI have lowered the barrier for impersonation. Deepfake audio and text allow attackers to mimic leadership voices and writing styles using limited source material. These messages often include urgency and requests to bypass normal approval steps.
Help desk impersonation receives special attention. Attackers study internal processes, then call support staff to request password resets or new MFA enrollment. In one observed scenario, a threat group escalated from initial social engineering to domain administrator access in about 40 minutes.
Services under the most strain
The study maps attacker motives to essential services that support the Games. Events management systems, hospitality platforms, payment services, transport networks, and utilities all appear as likely targets.
Disruption affects access to venues, schedules, and broadcasting. Financial attacks lead to fraud and data exposure. Espionage focuses on communications and surveillance. The interdependence of these services means an incident in one area can ripple across others.