encryption

Quantum encryption is pushing satellite hardware to its limits
In this Help Net Security interview, Colonel Ludovic Monnerat, Commander Space Command, Swiss Armed Forces, discusses how securing space assets is advancing in response to …

Retailers are learning to say no to ransom demands
Ransomware remains one of the biggest operational risks for retailers, but the latest data shows a shift in how these attacks unfold. Fewer incidents now lead to data …

Outdated encryption leaves crypto wide open
The cryptocurrency sector faces an existential threat on two fronts: none of the 2,138 web applications and 146 mobile apps tested by ImmuniWeb support post-quantum …

Apple strengthens storage flexibility with new disk image formats
Apple’s release of macOS 26 Tahoe introduced a new disk image format and updated an older one, both of which are drawing attention from system testers and forensic examiners. …

OpenSSL 3.6.0: New features, crypto support
The OpenSSL Project has announced the release of OpenSSL 3.6.0, a feature update that brings significant functionality improvements, standards compliance, and a few key …
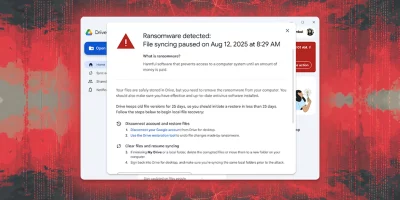
Google Drive for desktop will spot, stop and remedy ransomware damage
Google has rolled out AI-powered ransomware detection and file restoration features in Drive for desktop, Google’s official file syncing and access app for Windows and …

GitHub adds post-quantum protection for SSH access
GitHub is adding post-quantum cryptography to secure SSH connections, a move that signals the company’s preparation for a time when current encryption may no longer be safe. …

Nearly 500 researchers urge EU to rethink controversial CSAM scanning proposal
Nearly 500 scientists and researchers have signed an open letter warning that the latest version of the EU’s Chat Control Proposal would weaken digital security while failing …

Product showcase: iStorage datAshur PRO+C encrypted USB flash drive
The iStorage datAshur PRO+C is a USB-C flash drive featuring AES-XTS 256-bit hardware encryption. Available in capacities from 32 GB to 512 GB, the drive holds FIPS 140-3 …

Git 2.51: Preparing for the future with SHA-256
Git 2.51 is out, and the release continues the long process of modernizing the version control system. The update includes several technical changes, but one of the most …

NIST finalizes lightweight cryptography standard for small devices
The National Institute of Standards and Technology (NIST) has finalized a lightweight cryptography standard to protect even the smallest networked devices from cyberattacks. …

Product showcase: Apricorn Aegis NVX, a high-security, portable SSD
The Apricorn Aegis NVX is a hardware-based 256-Bit AES XTS external SSD drive with integrated USB-C cable. Its storage capacities range from 500GB to 2TB. The device is OS …