
Immutable Linux distribution Nitrux 6.0.0 adds GPU passthrough, boot-level recovery, C++ update system
Nitrux 6.0.0, released March 3, 2026, packages several components that security practitioners running Linux workstations will find worth examining: a new hypervisor …

Cybersecurity professionals are burning out on extra hours every week
Cybersecurity professionals in the U.S. are working an average of 10.8 extra hours per week beyond their contracted schedules, according to survey data collected from 300 …

mquire: Open-source Linux memory forensics tool
Linux memory forensics has long depended on debug symbols tied to specific kernel versions. These symbols are not installed on production systems by default, and sourcing them …

Why workforce identity is still a vulnerability, and what to do about it
Most organizations believe they have workforce identity under control. New hires are verified. Accounts are provisioned. Multi-factor authentication is enforced. Audits are …

Cybersecurity is now the price of admission for industrial AI
Industrial organizations are accelerating AI deployment across manufacturing, utilities, and transportation and running straight into a security problem. Cisco’s 2026 …

Coruna: Spy-grade iOS exploit kit powering financial crime
A powerful iOS exploit kit has circulated among multiple threat actors over the past year, moving from a commercial surveillance operation to state-linked espionage campaigns …

Threat actors weaponize OAuth redirection logic to deliver malware
An ongoing phishing campaign is abusing the OAuth authentication redirection mechanism to avoid triggering conventional email and browser defenses, Microsoft researchers have …
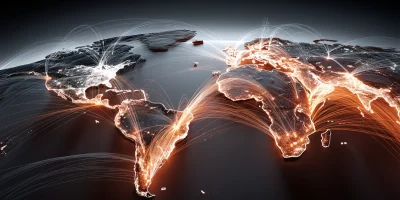
Cloudflare tracked 230 billion daily threats and here is what it found
Cloudflare’s network blocks over 230 billion threats per day. The volume indicates how routine and automated the attack cycle has become, and the patterns behind that …

$100 radio equipment can track cars through their tire sensors
When people consider what might track their movements, they think of smartphone apps, GPS services, or roadside cameras. The tires of a new car rarely enter that equation. …

Secure by Design: Building security in at the beginning
Secure by Design is not a single tool, product, or one‑time activity. It is a holistic approach that requires security to be deliberately embedded from the very beginning, at …

New Defender deployment tool streamlines Windows device onboarding with single executable
Microsoft’s Defender deployment tool for Windows helps administrators manage device onboarding at scale with updated progress visibility and additional controls. Onboarding …

Anthropic poaches users from rival chatbots with easier migration
The controversy over Anthropic’s negotiations with the Pentagon has driven increased interest in Claude. Negotiations between the Department of Defense and Anthropic collapsed …
Featured news
Resources
Don't miss
- Fake Claude Code install pages highlight rise of “InstallFix” attacks
- Decoding silence: How deaf and hard-of-hearing pros are breaking into cybersecurity
- Turning expertise into opportunity for women in cybersecurity
- Open-source tool Sage puts a security layer between AI agents and the OS
- Iran-linked APT targets US critical sectors with new backdoors