Top solutions to watch after RSAC 2025
RSAC 2025 showcased a wave of innovation, with vendors unveiling technologies poised to redefine cybersecurity. From AI-powered defense to breakthroughs in identity protection, this year’s conference delivered a glimpse into the future. Here are the most interesting products that caught our attention — and could shape what’s next.

Email authentication simplified: How PowerDMARC makes DMARC effortless

PowerDMARC helps organizations roll out DMARC the right way. They aim to make the setup simple, even for complex environments. With PowerDMARC, users can generate and publish DMARC, SPF, and DKIM records with a few clicks—no manual syntax editing or DNS guesswork needed. The platform validates entries in real time and alerts you if anything breaks authentication, ensuring seamless compliance.

Arctic Wolf launches Cipher to enhance security investigations with AI insights

Cipher is an AI security assistant that provides customers with self-guided access to deeper security insights directly within the Arctic Wolf Aurora Platform. Cipher enhances investigations and alert comprehension by delivering instant answers, contextual enrichment, and actionable summaries, all informed by real-world experience from Arctic Wolf’s AI-enabled global SOC.

LastPass Secure Access Experiences simplifies access management

Built with the needs of small-to-mid-sized businesses in mind, Secure Access Experiences represents a more unified, intuitive way to manage identity and access in a changing world — without the complexity, cost, or confusion that too often defines the category.

Abnormal AI improves security awareness training with AI agents

Abnormal AI introduced AI agents that not only protect people from advanced cyberattacks, but also eliminate the manual effort that’s bogging down security teams. From personalized phishing simulations to autonomous reporting and expanded threat remediation capabilities, these innovations represent a leap forward in how AI can be operationalized across the security stack.

Swimlane CAR solution automates compliance control mapping

Swimlane’s CAR Solution cuts through compliance audit complexity with AI automation that centralizes multi-framework control management, eliminates manual bottlenecks, streamlines evidence collection and fosters seamless collaboration between GRC and security teams.

BreachLock AEV simulates real attacks to validate and prioritize exposures

BreachLock AEV enables enterprises to launch automated multi-stage, complex red teaming engagements supercharged by generative AI across multiple threat vectors. Powered by threat intelligence, BreachLock Adversarial Exposure Validation users can leverage a constantly evolving library of Gen AI–created attack scenarios based on the latest adversarial techniques.

Saviynt ISPM provides insights into an organization’s identity and access posture

Built on Zero Trust principles, Saviynt’s ISPM incorporates all identity, access, activity, policies, configurations, events, and security signals into an AI-powered, enterprise-grade identity security data lake.

AVX ONE PQC Tool delivers crypto inventory, risk insights, and readiness scoring
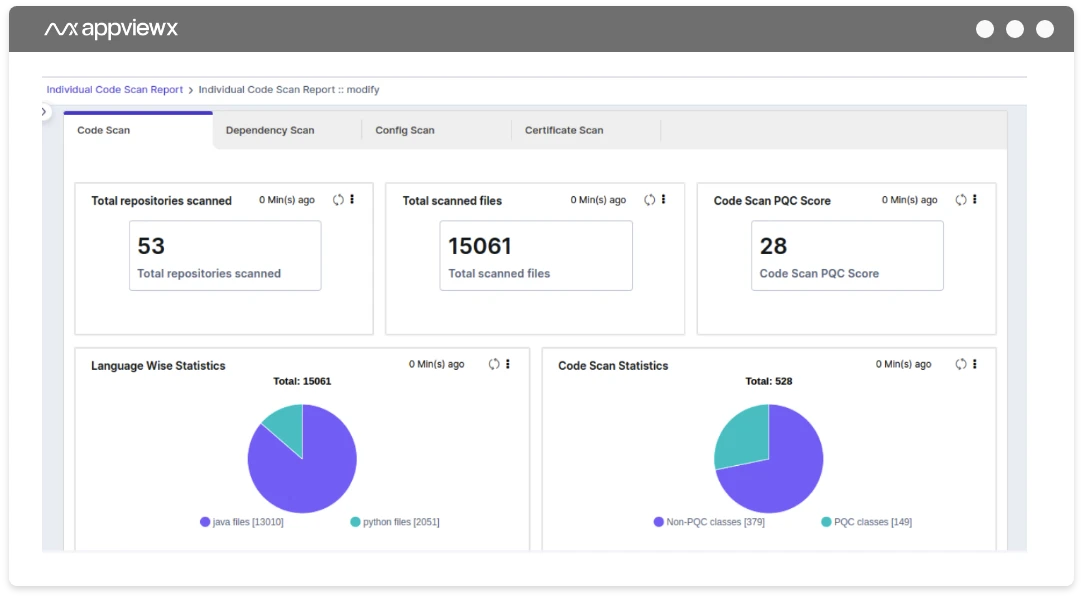
By scanning code, dependencies, configurations and certificates in enterprise environments, the PQC Assessment Tool provides visibility and an inventory of crypto assets to identify non-PQC compliant algorithms and risk. Additional PQC capabilities include a quantum-ready PKIaaS to issue PQC-safe certificates, automated CLM and crypto-agility, and secure code signing to ensure the validity and integrity of software.

Varonis AI Shield helps employees use AI without putting data at risk

Varonis AI Shield continuously analyzes your AI security posture, monitors how AI interacts with data, and dynamically right-sizes permissions so that sensitive information isn’t exposed due to poor data security hygiene. It makes intelligent decisions about which data to restrict from AI using Varonis’ patented permissions analysis algorithms that factor in data sensitivity, staleness, user profile, and more.

Flashpoint Ignite enhancements improve threat intelligence

Flashpoint announced new capabilities to its flagship platform, Flashpoint Ignite. These innovations are designed to deliver insights that align with customers’ threat intelligence needs, enabling organizations to make informed decisions and protect their most critical assets.
