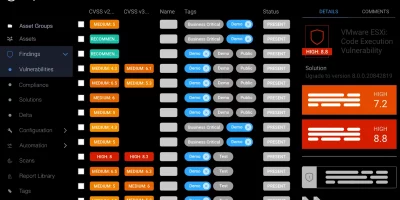
CyberFlex: Flexible Pen testing as a Service with EASM
About CyberFlex CyberFlex is an Outpost24 solution that combines the strengths of its Pen-testing-as-a-Service (PTaaS) and External Attack Surface Management (EASM) solutions. …

Five habits of highly secure development teams
In this Help Net Security video, Brendon Collins, Principal Consultant at Optiv, explores how organizations can embed security and privacy into the software development …

What the GitGuardian secrets sprawl report reveals about leaked credentials
In this Help Net Security video, Dwayne McDaniel, Senior Developer Advocate at GitGuardian, presents findings from The State of Secrets Sprawl 2025. McDaniel explains why …

AI isn’t taking over the world, but here’s what you should worry about
In this Help Net Security video, Josh Meier, Senior Generative AI Author at Pluralsight, debunks the myth that AI could “escape” servers or act on its own. He explains how …

How to build a secure AI culture without shutting people down
In this Help Net Security video, Michael Burch, Director of Application Security at Security Journey, explains how organizations can build a secure AI culture. He highlights …

DevOps in the cloud and what is putting your data at risk
In this Help Net Security video, Greg Bak, Head of Product Enablement at GitProtect, walks through some of the biggest security risks DevOps teams are dealing with. He covers …

What makes airport and airline systems so vulnerable to attack?
In this Help Net Security video, Recep Ozdag, VP and GM at Keysight Technologies, explains why airline and airport systems are so difficult to secure. He explores the complex …

Fighting fraud with AI: The new identity security playbook
In this Help Net Security video, Hal Lonas, CTO at Trulioo, talks about the rise of synthetic identity fraud and how it’s quickly becoming one of the biggest threats in …

What makes a security program mature and how to get there faster
Security leaders are flush with tools and data, but it’s not helping their programs mature. In this Help Net Security video, PlexTrac’s Dan DeCloss outlines the 3 key …

Third-party partners or ticking time bombs?
In this Help Net Security video, Ngaire Elizabeth Guzzetti, Technical Director Supply Chain at CyXcel, discusses why a third of U.S. organizations don’t trust …

AI in the SOC: Game-changer or more noise?
In this Help Net Security video, Kev Marriott, Senior Manager of Cyber at Immersive Labs, explores the challenges and opportunities of integrating AI into Security Operations …

What attackers know about your company thanks to AI
In this Help Net Security video, Tom Cross, Head of Threat Research at GetReal Security, explores how generative AI is empowering threat actors. He breaks down three key …
Featured news
Resources
Don't miss
- Your dependencies are 278 days out of date and your pipelines aren’t protected
- Security debt is becoming a governance issue for CISOs
- BlacksmithAI: Open-source AI-powered penetration testing framework
- When cyber threats start thinking for themselves
- IronCurtain: An open-source, safeguard layer for autonomous AI assistants