Infosec products of the month: June 2025
Here’s a look at the most interesting products from the past month, featuring releases from: Akamai, AttackIQ, Barracuda Networks, BigID, Bitdefender, Contrast Security, Cymulate, Dashlane, Embed Security, Fortanix, Fortinet, Jumio, Lemony, Malwarebytes, SpecterOps, StackHawk, Stellar Cyber, Sumsub, Thales, Tines, Vanta, and Varonis.


Bitdefender unifies security, risk management, and compliance in a single platform
Bitdefender announced GravityZone Compliance Manager, a new addition to its GravityZone platform that helps organizations reduce the burden of compliance and streamline audit readiness. The solution provides real-time visibility, automated remediation, audit-ready reports, and one-click compliance documentation fully integrated with Bitdefender endpoint security and risk analytics.


StackHawk Sensitive Data Identification provides visibility into high-risk APIs
Leveraging StackHawk’s existing API Discovery platform, which automatically uncovers APIs directly from source code repositories, Sensitive Data Identification enables security teams to prioritize testing of critical APIs handling sensitive data references, such as PII fields, cardholder data, and health information, based on both data sensitivity and rate of change.


Tines allows teams to choose the right AI level for any workflow
Unlike traditional AI implementations that require external data sharing or compromise on security, Tines’ agents run entirely within the platform’s secure infrastructure. This ensures no customer data leaves the environment, is logged, or used for training, delivering the privacy and governance assurances that enterprise teams demand.


Stellar Cyber updates MITRE ATT&CK Aligned Coverage Analyzer
Stellar Cyber announced its next-generation MITRE ATT&CK Aligned Coverage Analyzer, expanding the capabilities first introduced in the original Coverage Analyzer. This new version transforms visibility into strategy, providing security teams, CISOs, MSSPs, compliance officers, and insurance underwriters with precision in evaluating, optimizing, and communicating their threat detection posture.


SpecterOps Privilege Zones enables security teams to define logical access boundaries
Privilege Zones enable teams to define custom security boundaries around business-critical resources and enforce least privilege access continuously in on-prem, cloud and hybrid environments.


Dashlane’s AI model alerts businesses to phishing risks
In contrast to rule-based filters or reliance on a threat intel database, Dashlane’s AI phishing alerts leverage an AI model that analyzes 79 phishing indicators in real-time, such as hidden login forms, external link ratios and concealed iFrames, to determine whether a domain is potentially malicious. Analysis occurs directly on the user’s device, ensuring complete privacy protection.


Sumsub Device Intelligence offers protection against identity threats
Combined with behavioral analysis and device fingerprinting, Sumsub’s Device Intelligence considerably reduces false positives, which occur when legitimate users are mistakenly flagged as suspicious, while enhancing fraud detection accuracy across the whole user journey — from sign-up and login to transactions and profile changes.


BigID Vendor AI Assessment reduces third-party AI risk
Expanding on its capabilities in vendor management and third-party risk, BigID now enables organizations to assess not just who they do business with, but how those vendors are using AI and what impact that AI has on sensitive data. Unlike traditional governance tools that rely on static surveys, BigID discovers deployed models, maps them to the data they access, and provides actionable risk intelligence across AI usage, exposure, explainability, and regulatory readiness.


Jumio Liveness Premium combats deepfakes and injection attacks
Jumio’s premium solution leverages a patented Jumio technology, combining randomized color sequences and AI-driven analysis to confirm human presence in real time, effectively stopping spoofing attacks before they impact businesses.


Lemony mitigates privacy and compliance risks associated with cloud-based AI
With Lemony, different teams can run their own nodes or clusters of nodes and securely connect them. This enables teams to share knowledge across the organization, but only at the depth permitted by defined AI access policies. In other words, teams can tap into the expertise of others while maintaining strict control over what GenAI-generated knowledge is accessible.


Cymulate streamlines threat detection with AI-powered detection engineering assistant
Cymulate releaseed AI-powered detection engineering assistant for security information and event management (SIEM) rule threat coverage validation. By automating the correlation between detection rules and Cymulate attack scenarios leveraging advanced AI analysis, organizations can now ensure their SIEM rules are continuously validated against real-world threats and optimized with precision.


Vanta AI Agent automates time-consuming GRC workflows
The Vanta AI Agent autonomously handles end-to-end workflows across a company’s entire GRC program including identifying issues and inconsistencies individuals might miss and proactively taking action on their behalf—all while keeping teams informed and in control.


Thales File Activity Monitoring enhances enterprise control over unstructured data
File Activity Monitoring enables security teams to analyze and monitor the activity of unstructured data, including unexpected copying, downloading, and sharing of files such as emails, chat logs, media files, and application logs that can contain sensitive data.


Contrast Northstar pairs runtime data and contextual analysis with AI-powered auto-remediation
With the Northstar release, Security Operations and AppSec teams can see application-layer attacks as they happen, stop them instantly, and auto-remediate active vulnerabilities with the new Contrast AI.


BarracudaONE boosts threat protection and cyber resilience
BarracudaONE simplifies and strengthens security operations by unifying Barracuda’s portfolio of solutions into a single, integrated platform. It delivers layered threat protection, managed through a centralized dashboard, reducing operational complexity and improving visibility.


Akamai launches DNS Posture Management for real-time monitoring and guided remediation
Akamai DNS Posture Management provides real-time monitoring and guided remediation across all major DNS providers. Security teams can detect and respond to DNS-based attacks, certificate security risks, vulnerabilities, and misconfigurations that weaken an organization’s security posture.


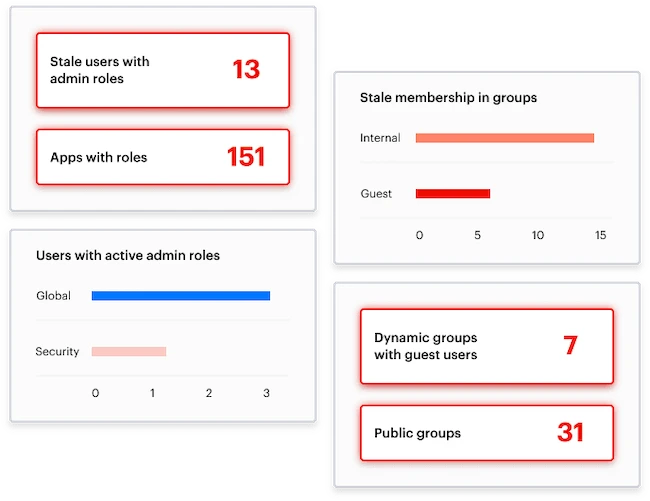
Varonis Identity Protection resolves identity posture issues
Varonis Identity Protection monitors identity providers for signs of compromise, alerting on suspicious logins, password resets, MFA changes, and policy updates — in context with each account’s data access activity.

FortiMail Workspace Security expands protection beyond email to web and collaboration tools
FortiMail can address any email security needs, including inbound, outbound (including relays), and internal mail protection, with flexible deployment options across appliances, virtual machines, hosted services, and SaaS. It offers multiple operating modes—gateway, server, ICES, and hybrid—and features both a highly configurable UI and a streamlined SaaS experience.


AttackIQ Ready3 identifies which vulnerabilities are truly exposed
With expanded discovery capabilities, Ready3 maps both internal and external attack surfaces. By correlating asset discovery with vulnerability context, attack paths and compensating controls, the platform helps security teams identify which vulnerabilities are truly exposed because existing defenses are failing to stop them.


Fortanix PQC Central boosts post-quantum readiness
Embedded in Key Insight, which handles cryptographic discovery and risk assessment within the Fortanix Armor platform, PQC Central helps organizations turn PQC migration complexity into actionable insights and strategic priorities.


Embed’s agentic security platform triages and investigates security alerts
Unlike AI SOC solutions that rely on generic, off-the-shelf AI models, Embed’s AI agents are purpose-built and trained on actual security investigations, enabling them to reason like expert SOC analysts while maintaining complete visibility into their decision-making process.

Malwarebytes Scam Guard spots and avoids potential scams
Whether it’s a suspicious text, DM, email, image or link, Scam Guard offers judgment-free, personalized advice to help users spot and avoid potential scams. Embedded within the Malwarebytes Mobile Security app, the new feature aims to remove the stigma of shame around scams by helping educate and guide users before it’s too late.

