Infosec products of the month: April 2025
Here’s a look at the most interesting products from the past month, featuring releases from: 1touch.io, Abnormal AI, AppViewX, Arctic Wolf Networks, Bitdefender, BitSight, Bugcrowd, Cato Networks, CyberQP, Cyware, Entrust, Exabeam, Flashpoint, Forescout, Index Engines, Jit, LastPass, PlexTrac, PowerDMARC, RunSafe Security, Saviynt, Seal Security, Seemplicity, Skyhawk Security, Stellar Cyber, Swimlane, Varonis, and Veracode.


Email authentication simplified: How PowerDMARC makes DMARC effortless
With PowerDMARC, users can generate and publish DMARC, SPF, and DKIM records with a few clicks—no manual syntax editing or DNS guesswork needed. The platform validates entries in real time and alerts you if anything breaks authentication, ensuring seamless compliance.


Skyhawk Security enhances Autonomous Purple Team to secure custom cloud apps
With its latest expansion, the Skyhawk platform will now preemptively analyze and detect application-layer vulnerabilities, evaluate exploit paths across application and infrastructure boundaries and prioritize remediation based on real-time risk context. It will also continuously monitor for threats, including exploits that cross between applications and cloud infrastructure. All without the need for agents and their associated costs and complexity.


Stellar Cyber boosts security operations with human-augmented Autonomous SOC
Stellar Cyber’s new Autonomous SOC brings clarity to chaos by automating detection, triage, and response across the full attack surface while empowering analysts with AI-driven insight. At the heart of Stellar Cyber’s innovation is Agentic AI—a collaborative system of specialized, multi-layered agents trained to work alongside humans rather than replacing them.


Bitdefender GravityZone PHASR sets new standard for endpoint security solutions
Bitdefender GravityZone Proactive Hardening and Attack Surface Reduction (PHASR) is an endpoint security solution that dynamically tailors hardening for each user, ensuring that security configurations align with user-intended privileges and behaviors and adapt to shrink attack surfaces.


Jit launches AI agents to ease AppSec workload
Jit has launched its new AI agents to offload specific and tedious tasks from AppSec teams such as creating risk assessments, threat models, and compliance reports; while making it easy to take action on mitigating security risk. As a result, AppSec teams can keep pace with the risks that are being introduced faster than ever due to AI code-generation tools.


Swimlane CAR solution automates compliance control mapping
Swimlane’s CAR Solution cuts through compliance audit complexity with AI automation that centralizes multi-framework control management, eliminates manual bottlenecks, streamlines evidence collection and fosters seamless collaboration between GRC and security teams.


Veracode platform enhancements improve software security
Veracode announced new capabilities to help organizations address emerging threats, giving security professionals better visibility and control in one place. The launch includes new AI-powered functionality in the Dynamic Application Security Testing (DAST)product and an External Attack Surface Management (EASM) capability.


PlexTrac for CTEM helps security teams centralize security data
PlexTrac for CTEM enables both enterprises and Managed Security Service Providers (MSSPs) to streamline security operations, unify cross-functional teams within a centralized platform, strengthen threat exposure management, and demonstrate measurable improvements in their overall security posture.


Entrust Cryptographic Security Platform provides visibility into cryptographic risk posture
The Entrust Cryptographic Security Platform integrates capabilities to deliver unified compliance management, PKI deployment and operation, and lifecycle management for keys, secrets, and certificates, secured with Entrust nShield and third-party hardware security modules (HSMs) and interoperable with top security, identity, and IT management systems through extensive integrations, providing for protection.


Seemplicity adds AI-driven capabilities to scale remediation operations
The latest version of the Seemplicity Platform introduces new AI-driven capabilities designed to streamline and scale remediation operations. Two major new features – called “Find the Fixer” and “Automatic Scoping” – reduce remediation chaos by eliminating manual bottlenecks and accelerate the path from detection to resolution.


Cato Networks unveils GenAI security controls for Cato CASB
Cato CASB, a native feature in the Cato SASE Cloud Platform, is now enhanced with new capabilities for GenAI applications including a shadow AI dashboard and policy engine. With the shadow AI dashboard, enterprises can detect, analyze, and gain insights into the use of GenAI. With the policy engine, enterprises can take control of user activities in GenAI applications.


Cyware strengthens threat intelligence management
Cyware has added Compromised Credential Management to the Cyware Intel Packaged Solution, a pre-configured threat intelligence program-in-a-box that enables security teams to operationalize threat intelligence faster by eliminating complex integrations and configurations.


RunSafe Risk Reduction Analysis offers insights into memory-based CVEs
RunSafe Security launched the RunSafe Risk Reduction Analysis, which analyzes total exposure to Common Vulnerabilities and Exposures (CVEs) and memory-based zero days in software. Designed for cybersecurity professionals and embedded systems developers, the solution provides insight into system vulnerabilities as well as data on how runtime mitigations can drastically reduce software exposure.


Index Engines CyberSense 8.10 strengthens AI-driven cyber resilience
CyberSense 8.10 brings deeper visibility into organizational data integrity, ensuring the detection of corrupted data, and allows organizations to pinpoint the last known clean backup, to minimize the impact of an attack. This latest release also empowers organizations with expanded role-based access control with custom permissions as well as improved threshold alerts and UI/UX improvements.


Forescout eyeScope provides organizations with insight into their security posture
Forescout eyeScope provides network, security and incident response teams with a consolidated, up-to-date view of their device landscape with classification, connection, and compliance context through a cloud-enabled solution that can be installed in a fraction of the time compared to traditional solutions.


Seal Base Images mitigates container vulnerabilities
Seal Base Images provides a unified platform to remediate vulnerabilities across IT systems, backend infrastructure, and application code, enabling organizations to secure existing legacy systems while future-proofing their environments.


Exabeam Nova accelerates threat detection and response
By correlating multiple detections within a case and using a proprietary threat classification framework, Exabeam Nova distinguishes between compromised insiders, malicious insiders, and undetermined threats with precision, enabling security teams to quickly identify, investigate and respond to threats with greater efficiency and accuracy.


CyberQP launches Zero Trust Helpdesk Security Platform
CyberQP has launched Zero Trust Helpdesk Security Platform, combining QGuard for Privileged Access Management (PAM) and QDesk for End-User Access Management (EUAM). A key innovation of the platform is End-User Elevation, which allows users to gain temporary admin access without persistent privileges. By automating approval processes and monitoring activity in real-time, CyberQP reduces attack surfaces while maintaining security and compliance.


1touch.io helps organizations safeguard sensitive data
1touch.io launched the next-generation Enterprise Data Security Posture Management (DSPM) platform. By integrating continuous data discovery, real-time access intelligence, AI-powered risk prioritization, and policy-driven orchestration into a unified platform, 1touch.io delivers business value to organizations by reducing security risks, optimizing compliance operations, and enabling digital transformation at scale.


Bitsight Identity Intelligence provides visibility into compromised accounts
Bitsight launched Bitsight Identity Intelligence, a new, standalone threat intelligence module designed to help security teams detect compromised credentials, prevent unauthorized access, and proactively mitigate risk across their extended attack surface.


LastPass Secure Access Experiences simplifies access management
Built with the needs of small-to-mid-sized businesses in mind, Secure Access Experiences represents a more unified, intuitive way to manage identity and access in a changing world — without the complexity, cost, or confusion that too often defines the category.


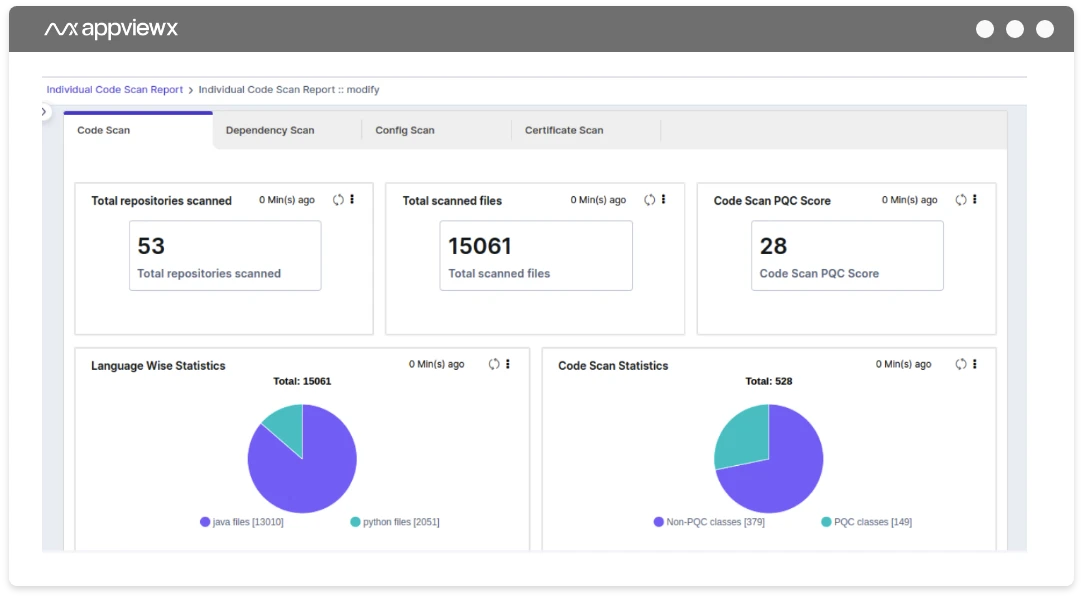
AVX ONE PQC Tool delivers crypto inventory, risk insights, and readiness scoring
By scanning code, dependencies, configurations and certificates in enterprise environments, the PQC Assessment Tool provides visibility and an inventory of crypto assets to identify non-PQC compliant algorithms and risk. Additional PQC capabilities include a quantum-ready PKIaaS to issue PQC-safe certificates, automated certificate lifecycle management (CLM) and crypto-agility, and secure code signing to ensure the validity and integrity of software.

Flashpoint Ignite enhancements improve threat intelligence
Flashpoint announced new capabilities to its platform, Flashpoint Ignite. These innovations are designed to deliver insights that align with customers’ threat intelligence needs, enabling organizations to make informed decisions and protect their most critical assets.


Saviynt ISPM provides insights into an organization’s identity and access posture
Saviynt launched AI-powered Identity Security Posture Management (ISPM) as part of its converged Identity Cloud platform. Built on zero trust principles, Saviynt’s ISPM incorporates all identity, access, activity, policies, configurations, events, and security signals into an AI-powered identity security data lake.


Varonis AI Shield helps employees use AI without putting data at risk
Varonis AI Shield continuously analyzes AI security posture, monitors how AI interacts with data, and right-sizes permissions so that sensitive information isn’t exposed due to poor data security hygiene.


Bugcrowd enables organizations to test their security environments
Available on the Bugcrowd Platform, RTaaS works alongside offerings such as Penetration Testing as a Service, Managed Bug Bounty, and Vulnerability Disclosure Programs. Bugcrowd customers can tailor their RTaaS engagements to meet specific needs, budget constraints, and organizational maturity.


Arctic Wolf launches Cipher to enhance security investigations with AI insights
Arctic Wolf has introduced Cipher, an AI security assistant that provides customers with self-guided access to deeper security insights directly within the Arctic Wolf Aurora Platform. Cipher enhances investigations and alert comprehension by delivering instant answers, contextual enrichment, and actionable summaries, all informed by real-world experience from Arctic Wolf’s AI-enabled global security operations centers (SOC).


Abnormal AI improves security awareness training with AI agents
Abnormal AI introduces autonomous AI agents that improve how organizations train employees and report on risk while also evolving its email security capabilities. Abnormal’s newest innovations bring intelligent automation to security awareness training, executive reporting, and advanced email threat detection.

